Most security operations center (SOC) and incident response (IR) teams are overwhelmed and understaffed, often scrambling to reactively chase threats with firewall blocklists in a futile game of cat-and-mouse. Fortunately, by leveraging higher-level cyber threat intelligence (CTI) that maps out specific tactics, techniques, and procedures (TTPs) in alignment with the kill chain, your SOC can intelligently and proactively block these threats and even prevent future threats.
Becoming more proactive requires you to pivot from the "what" to the "how" of the attack. As we discussed in "Shifting from What to How to Get Ahead of the Threat," making this change positions your CTI, SOC, and IR teams to track down not just what has happened, but also to block future attacks.
Shifting from what to how requires adjustment
Getting from "what" to "how" is not as simple as having your CTI team send over lists of MITRE ATT&CK® techniques to SOC and IR staff. A standalone ATT&CK technique with no additional context is worthless to a stressed-out SOC or IR analyst trying to identify something serious like a potential command-and-control (C2) channel. This analyst needs context around the techniques to answer these questions: Why should I care right now? How does this relate to other things the SIEM may, or may not, be telling me? How does this threat intelligence help me mitigate the intrusion? This context comes from a shared understanding of the attack TTPs, their potential impact on the organization, and how best to mitigate them. Achieving this shared understanding requires tightly aligning your CTI, SOC, and IR teams.
Based on working with some of the most targeted organizations in the world, we see three essential areas of focus to synch these teams: platform, performance, and protocol.
A platform to develop actionable threat intelligence
Unfortunately, most organizations are still managing threat intelligence using standard office tools. To underscore this point, the SANS 2022 CTI survey revealed that the bulk of respondents rely on spreadsheets and emails as the primary means to aggregate, analyze, and present CTI information!1
The complexity of processing millions of indicators, intelligence reports, and internal telemetry findings and managing the relationships among these data points requires much more than Microsoft Excel and a SIEM. Plus, your CTI team must do more than process this data. They need to support the organization's priority intelligence requirements (PIR) by aligning this information to sophisticated threat models like the diamond model of intrusion analysis and the MITRE ATT&CK® framework. This alignment positions your CTI analysts to produce actionable threat intelligence reports covering the broader attack picture.
What your analysts require is help consolidating extensive threat information by automatically deduplicating, normalizing, and structuring it and then delivering this structured intelligence into community of interest workspaces that facilitate analysis and collaboration. For example, EclecticIQ Intelligence Center provides your CTI analysts with an advanced threat intelligence manager, curated threat detection content, intelligence feeds, tools integration, and a collaborative analyst workbench. With these capabilities, your analysts can collect and process data, create and share CTI, and accelerate detection and response.
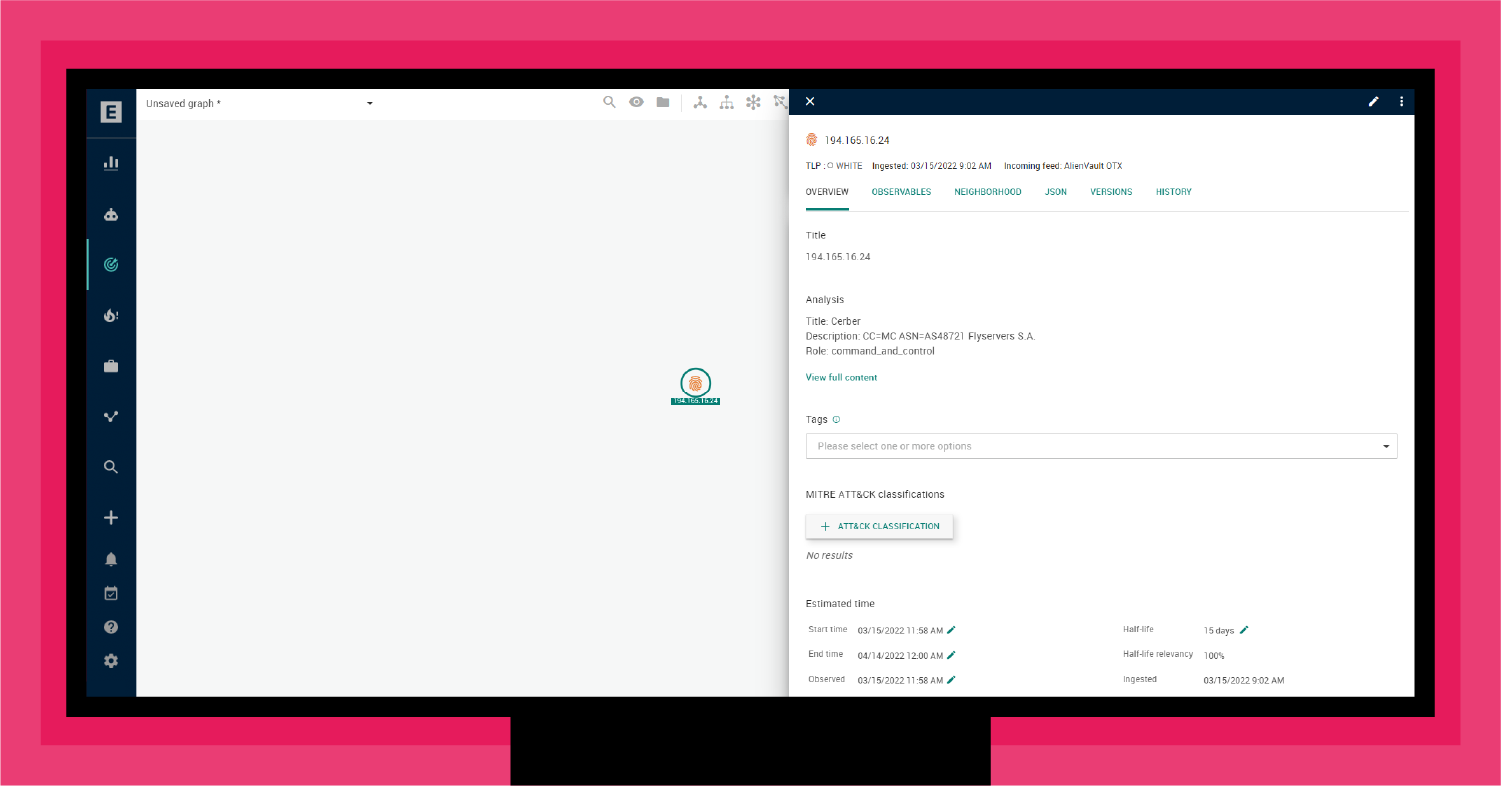
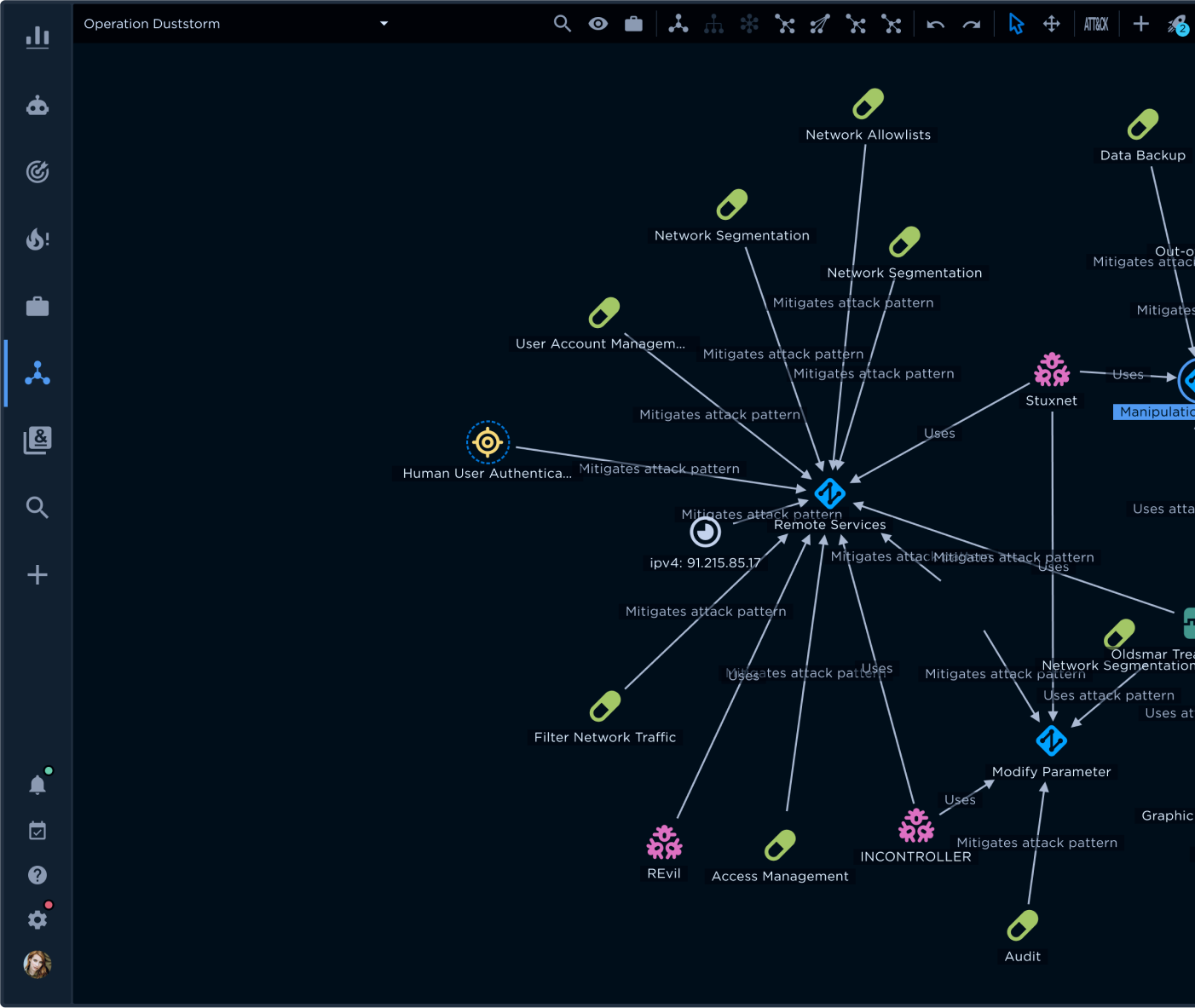
To illustrate this process, as shown in Figure 1, your CTI team may receive a suspicious indicator that could be an active C2 channel.
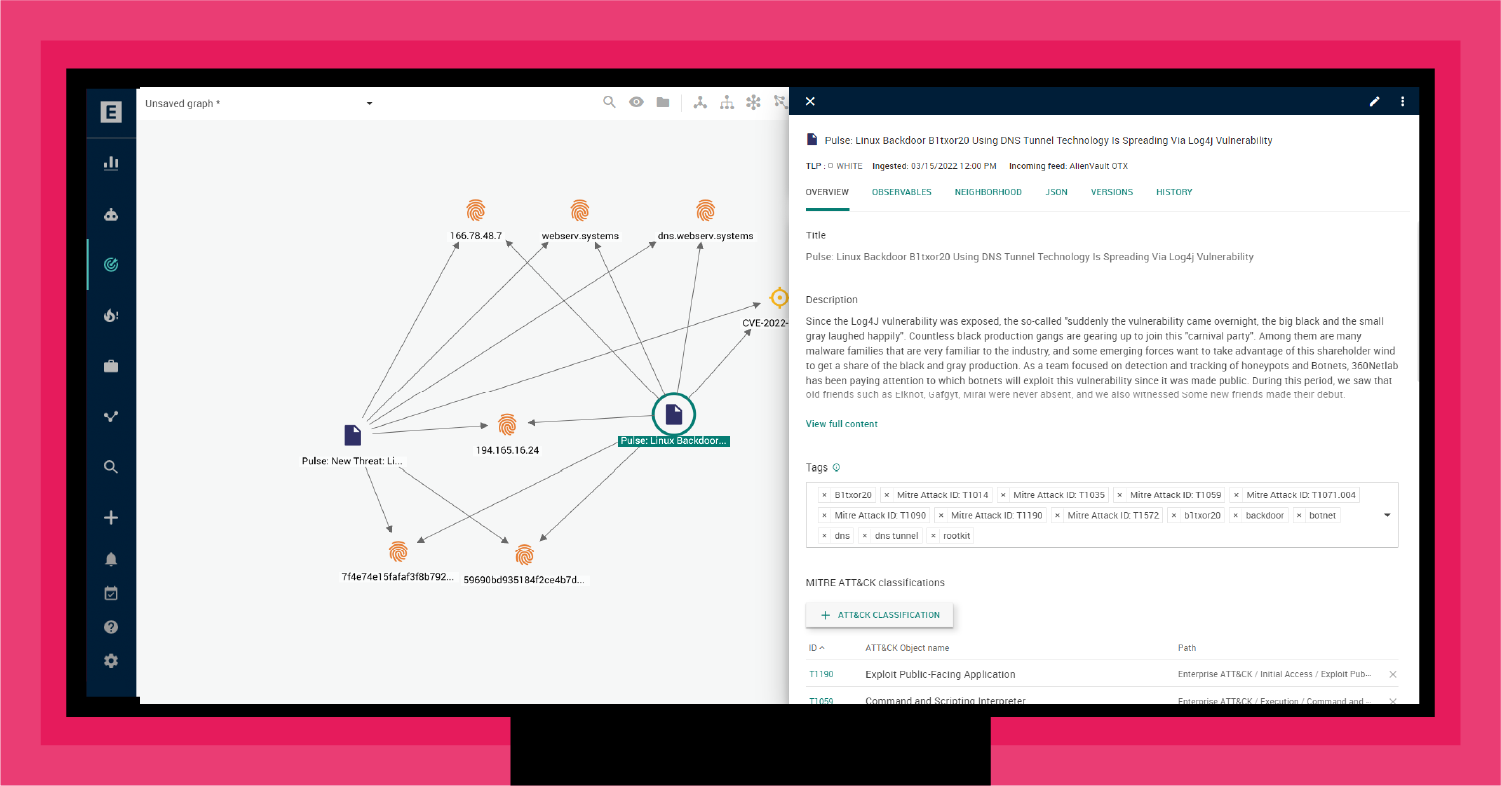
An analyst would then expand the analysis to see what TTPs and threat actors are associated with this indicator. As shown in Figure 2, for this C2 channel, there is alignment with the Log4j vulnerability. Specifically, a new botnet appears to use the Log4j vulnerability to create a backdoor trojan for the Linux platform. The trojan uses DNS Tunnel technology to build the C2 communication channel. As the analysis points out, "It is very convenient to turn the invaded device into a springboard for subsequent infiltration."2
Making this connection between an indicator and a potential botnet exploiting Log4j as a backdoor trojan for Linux platforms is helpful. However, it is not yet actionable. To be actionable, your CTI analyst must understand the TTPs associated with this attack and assess their role in the overall kill chain. For this, the CTI team can turn to MITRE ATT&CK®.
Aligning with MITRE ATT&CK
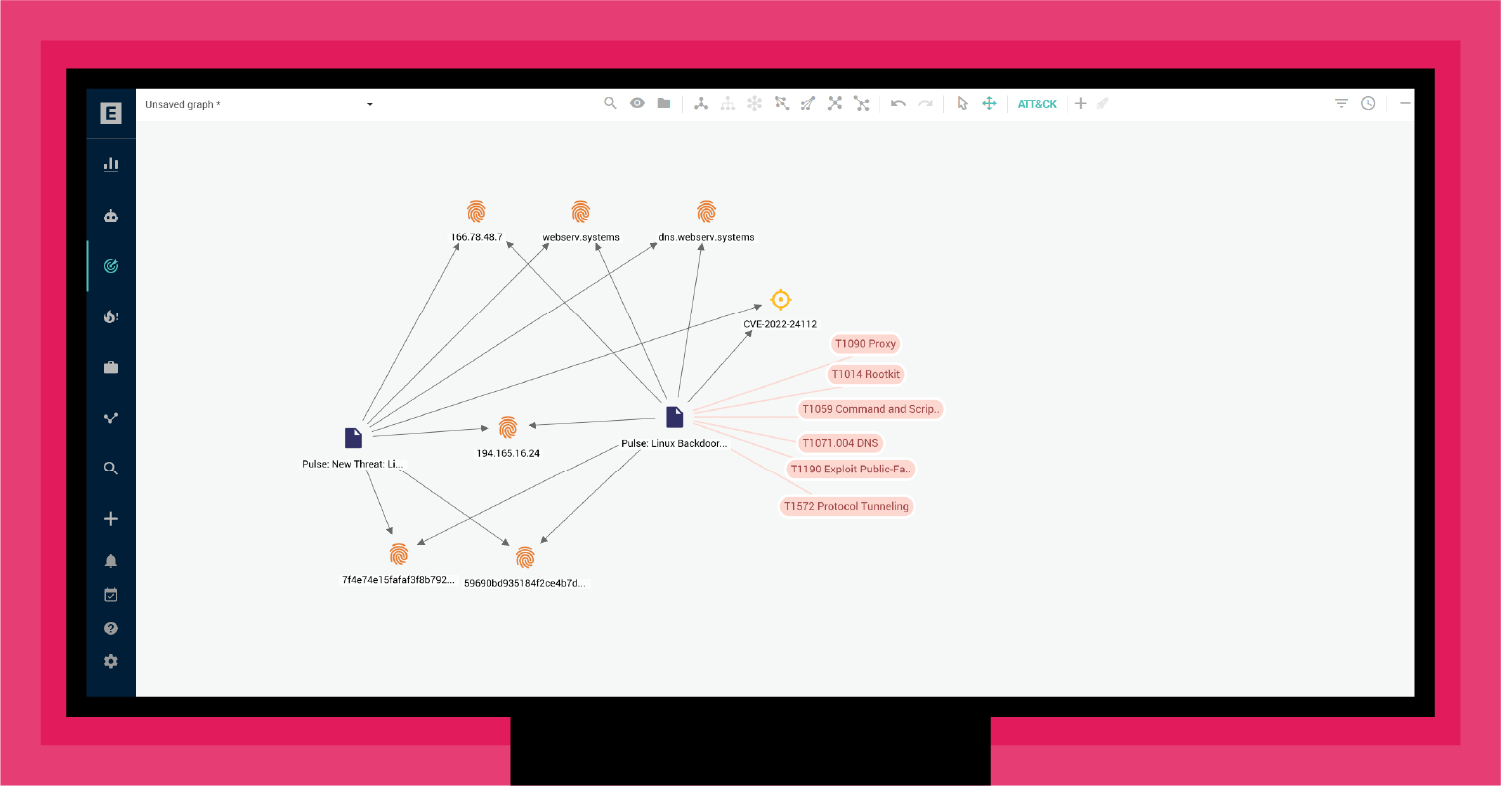
As shown in Figure 3, EclecticIQ Intelligence Center automatically extracts MITRE ATT&CK® techniques from the threat intelligence to provide directional guidance. As discussed in "Three Strategic Steps to a Threat-informed Defense (TiD)," MITRE ATT&CK® delivers a means to align TTPs with vulnerabilities, infrastructure, threat actors, and mitigation techniques.
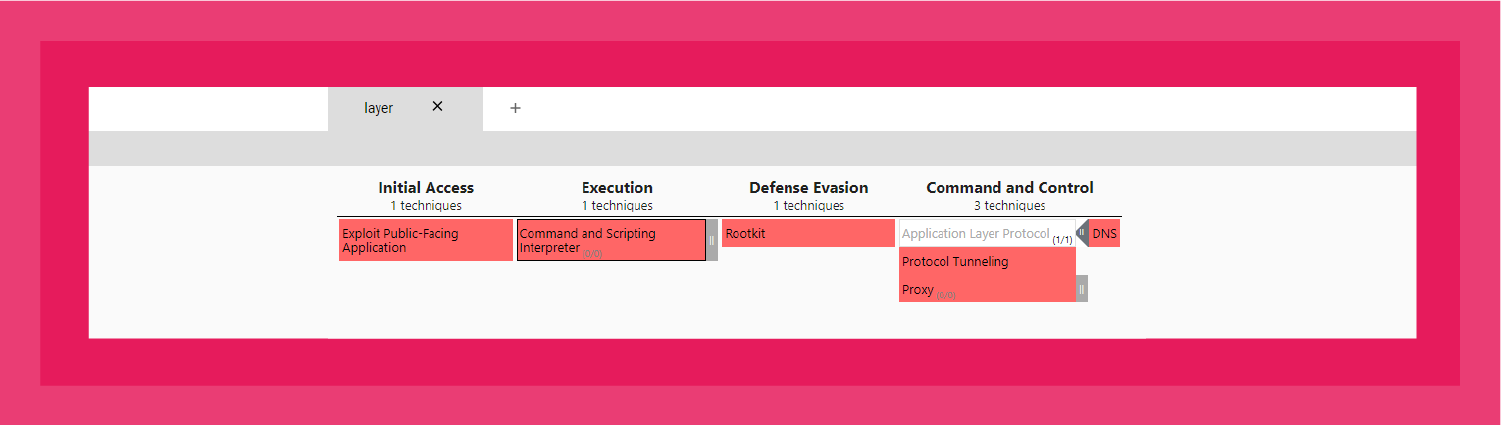
Mapping these techniques to MITRE ATT&CK Navigator (see Figure 4) provides a snapshot of the TTPs that align with this backdoor trojan. Specifically, this attack typically starts with an outward-facing application exploit, followed by abusing a command and script interpreter (e.g., Unix Shell), dropping a rootkit, and then exploiting DNS tunneling to establish a C2 channel.
This alignment provides the SOC and IR teams with actionable information to identify TTPs throughout the kill chain.
A performance boost for SOC and IR with Knowledge Packs
With a better threat assessment, the next step is pivoting to identify the scope of the attack and determine if there are any other exploits of Log4j that might be active. This process requires threat hunting.
Threat hunting, as a practice, has been around for a long time. It initially emerged as a manual process in which experts create a set of hypotheses that they use to interrogate the organization's controls and assets to look for active threats. Essentially, this process requires the hunters to use their knowledge of TTPs to look for evidence of common techniques that adversaries use, particularly against specific vulnerabilities.
As one can imagine, this is a needle in a haystack practice that involves hours of tedious research and sifting through terabytes of telemetry (e.g., logs, scans, threat feeds). The goal of the threat hunter is to find a previously undetected compromised system.
Still, threat hunting is a growing activity in most SOCs. SANS found that more than three-quarters of all organizations will have active threat hunting operations in the foreseeable future.3
To help CTI, SOC, and IR teams achieve more successful threat hunting, EclecticIQ Intelligence Center provides Knowledge Packs. Knowledge Packs contain essential information to hunt down potential exploits of a vulnerability or situation. The Knowledge Pack automatically organizes the information in EclecticIQ Intelligence Center to bring together relevant data.
The EclecticIQ Threat Research Team develops Knowledge Packs on an ongoing basis based on data from a broad range of intelligence sources: in-house and external. Knowledge Packs typically align with new malware families that are active in the wild or the relaunch of variants as fresh attacks.
When you click on the Knowledge Pack, EclecticIQ Intelligence Center generates a dedicated workspace on the fly. This way, you can instantly start tracking relevant, timely threats without spending any time or effort manually configuring the workspace and collecting intelligence.
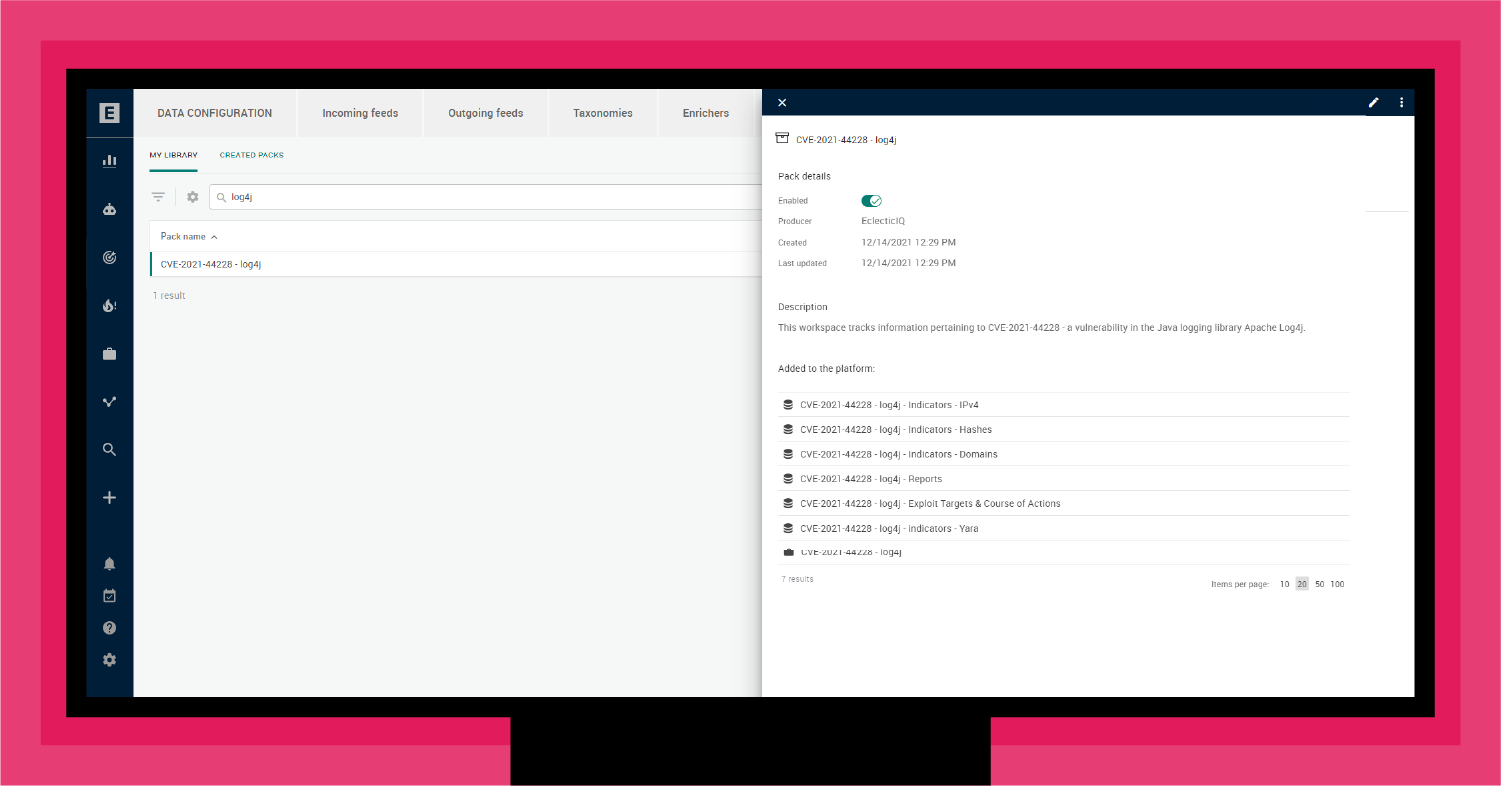
As shown in Figure 5, a Knowledge Pack includes pre-configured rules and datasets on specific topics that EclecticIQ Intelligence Center customers can download. For example, shortly after the announcement of the Log4j vulnerability (CVE-2021-44228), the EclecticIQ Threat Research Team created a Rapid Alert for clients, followed by a Knowledge Pack for Log4J.
For many organizations, the Knowledge Pack is the first step in conducting active threat hunting. In the future, EclecticIQ will be releasing hunting packs to accelerate threat hunting for CTI and SOC teams.
A protocol for CTI-SOC-IR communications
What ultimately makes shifting from "what" to "how" possible is a much tighter alignment of CTI-SOC-IR communications to develop and share actionable intelligence. Specifically, we see a natural three-stage evolution that organizations go through.
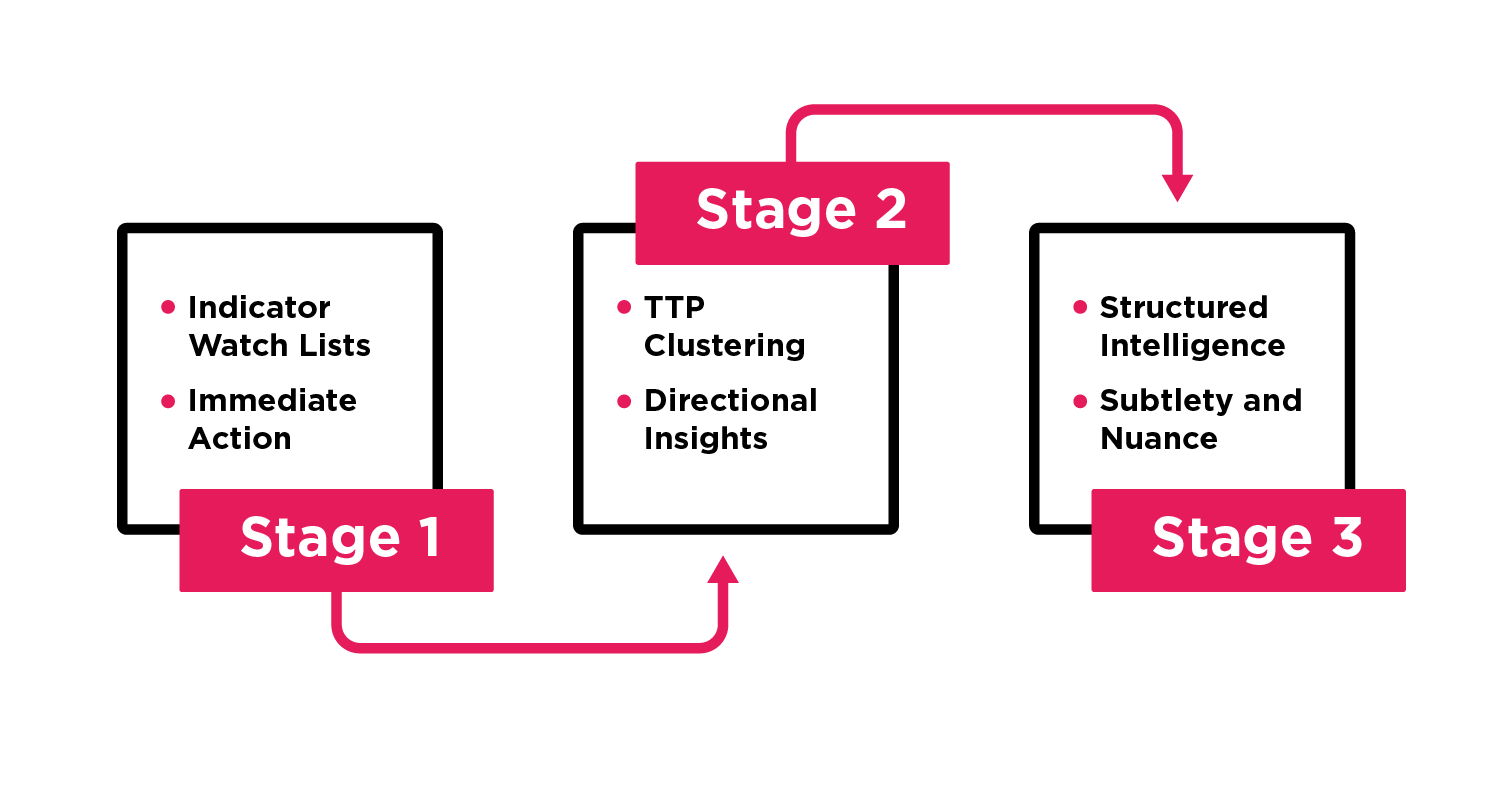
Stage 1 – Indicator watch lists for immediate action
Shifting to TTPs does not mean moving away from indicator watch lists. Watch lists are still essential since the security team often works at higher revolutions per minute (RPMs) than the CTI team. Because of this disparity, the security team will always press for quick, easily ingestible indicators that they can deploy to their security controls. What changes with the TTP focus is the content of the watch list. Rather than raw IOCs (i.e., think low-level on the pyramid of pain), the CTI watch list contains indicators aligned with higher-level constructs such as tools and TTPs. Blocking a TTP is quite effective since it pushes the adversary to switch their modus operandi: an expensive proposition. The key to success at this stage is getting security and CTI to agree on what goes into the watch list.
Stage 2 – TTP Clustering around context for directional insights
Aligning TTPs around context is paramount when CTI and SOC teams shift from "what" to "how." Without this alignment, teams waste resources reactively trying to block everything that moves. For example, an indicator on the watch list could associate with malware for initial access via phishing, or it might indicate a process injection for lateral movement via a remote services technique. Understanding which approach is more likely is essential to establishing the correct threat response.
In the former case, the appropriate response would be anti-phishing controls, and for the latter, it would be detecting/blocking lateral movement and locking down RDP ports. Directional guidance from the CTI team is essential for the SOC to determine the right action.
As discussed in our blog, "How to Use MITRE ATT&CK to Map and Track Adversary TTPs," the MITRE ATT&CK® framework is critical in helping organizations develop a standard protocol for teams to use in aligning TTPs around context.
Stage 3 – Structured intelligence to impart subtlety and nuance
The highest level of communication between the CTI and security teams uses structured intelligence. There is much subtlety and nuance necessary to explain the "how." For example, just passing over a list of TTPs leaves significant gaps of understanding between the analyst and the consumer of the intelligence. In other words, accurately describing a multi-layered, asymmetric, and repeated attack with just a list of TTPs is nearly impossible. Instead, using a structured form that lays out tactics, techniques, historical context, and even mitigation approaches, can help impart a common understanding of the facts of the attack.
Delivering structured intelligence relies on a common ontology describing the complete kill chain. The most comprehensive model is MITRE ATT&CK®. With MITRE ATT&CK®, analysts develop threat intelligence that puts TTPs in the context of the overall attack, focusing on specific threat actors and groups and aligning with the organization's infrastructure and vulnerabilities. This structured intelligence is the protocol on which your SOC and IR team can shift their focus from reactive to proactive operations.
Aligning your CTI, SOC, and IR Teams for proactive operations
Going from "what" to "how" is a complex process, but even small shifts toward focusing on TTPs can have significant results. By implementing a threat intelligence management solution that supports consolidation and normalization of all threat and telemetry information and aligns data to TTPs, CTI analysts can produce actionable threat intelligence that sharpens their team's response to new threats. To use this intelligence to its best advantage, CTI, SOC, and IR teams must implement a common communication protocol. With platform, process, and protocol in place, organizations can use advanced capabilities like EclecticIQ Knowledge Packs to track down active threats. The result of shifting to a TTP focus is better communications and coordination between CTI, SOC, and IR teams and more proactive operations.
Footnotes
- SANS 2022 CTI Survey, February 2022, page 2.
- https://blog.netlab.360.com/b1txor20-use-of-dns-tunneling_cn/
- SANS 2021 SOC Survey