Driven mainly by a defense-in-depth mentality, most organizations protect the network by blocking adversaries at the network edge. This means that the security operations center (SOC) must continually update its firewall blocklists to stop adversaries in their tracks. Blocklists rely on a continual flow of low-level indicators of compromise (IOC). Of course, Zero Trust security is shifting this model to a never-trust-always-verify model, but most day-to-day security operations revolve around blocklists.
Does this sound familiar? Like a perpetual game of cat-and-mouse, these blocklists attempt to stop adversaries, hopefully before they've breached your network. It's not working. Your SOC analysts are undoubtedly overloaded and ineffective because they are suffering from alert fatigue driven by IOCs.
Even if your SOC could continually process the firehose of IOCs, blocklists built from those IOCs will miss all but the most basic of attacks. Even then, the attacks may have already caused significant damage before detection. There are three drawbacks with blocklists based on IOCs:
- They represent IOCs that are easy to alter (e.g., hashes, domains, IP addresses), meaning there is a minimal cost for the adversary to pivot and invalidate the firewall rule.
- IOCs tend to arise during the later phases of the kill chain. In other words, by the time your CTI team delivers an IOC, the adversary may already be three moves ahead (e.g., lateral movement, escalated privileges).
- IOCs are unreliable. Adversaries circumvent blocklists by ensuring that any IOCs they generate do not trigger malware or hash signatures. They may even inject false IOCs to throw off your CTI analysts.
It's time to shift from what to how
To address these challenges, your organization must shift the way it produces and processes threat information. Specifically, you must move from focusing on "what" is happening to "how" the attack is happening. This is not a trivial task.
By tracking IOCs, your SOC team rarely sees an attack as it happens. Instead, they're almost always in reaction mode, focusing on what has already occurred. By including the tactics, techniques, and procedures (TTPs) behind the attack, your SOC gains essential context that helps to better define what happened. It also helps determine what might be going on right now and what might happen in the future.
To illustrate, your SOC staff may see an IP address and port indicator that could be a command-and-control (C2) channel (the "what"). Or it might be a false indicator. Because of this uncertainty, the team lacks sufficient information to decide whether to block the address. Understanding that an attacker habitually uses protocol tunneling as a C2 technique (the "how") provides directional information that leads your SOC to capture network flows. These network flows can then provide the evidence necessary to confidently block the port.
Determining the "how" of an attack requires you to look beyond IOCs to TTPs. By describing an attacker's behavior, methods, and patterns, TTPs provide a comprehensive intelligence picture with greater context. This picture still includes IOCs, but it also contains observables and MITRE ATT&CK® taxonomy to help different teams understand attacks at strategic and operational levels.
Shifting from "what" to "how" is an intelligent move because threat actors tend to execute attacks in repetitive ways. They often rely on attack patterns that are historically effective against a particular victim or set of victims. Knowing what's effective for the attacker helps position you to block their next move.
Where's the pain
It is harder for an adversary to change tactics and techniques when you zoom in on how they execute the attack.
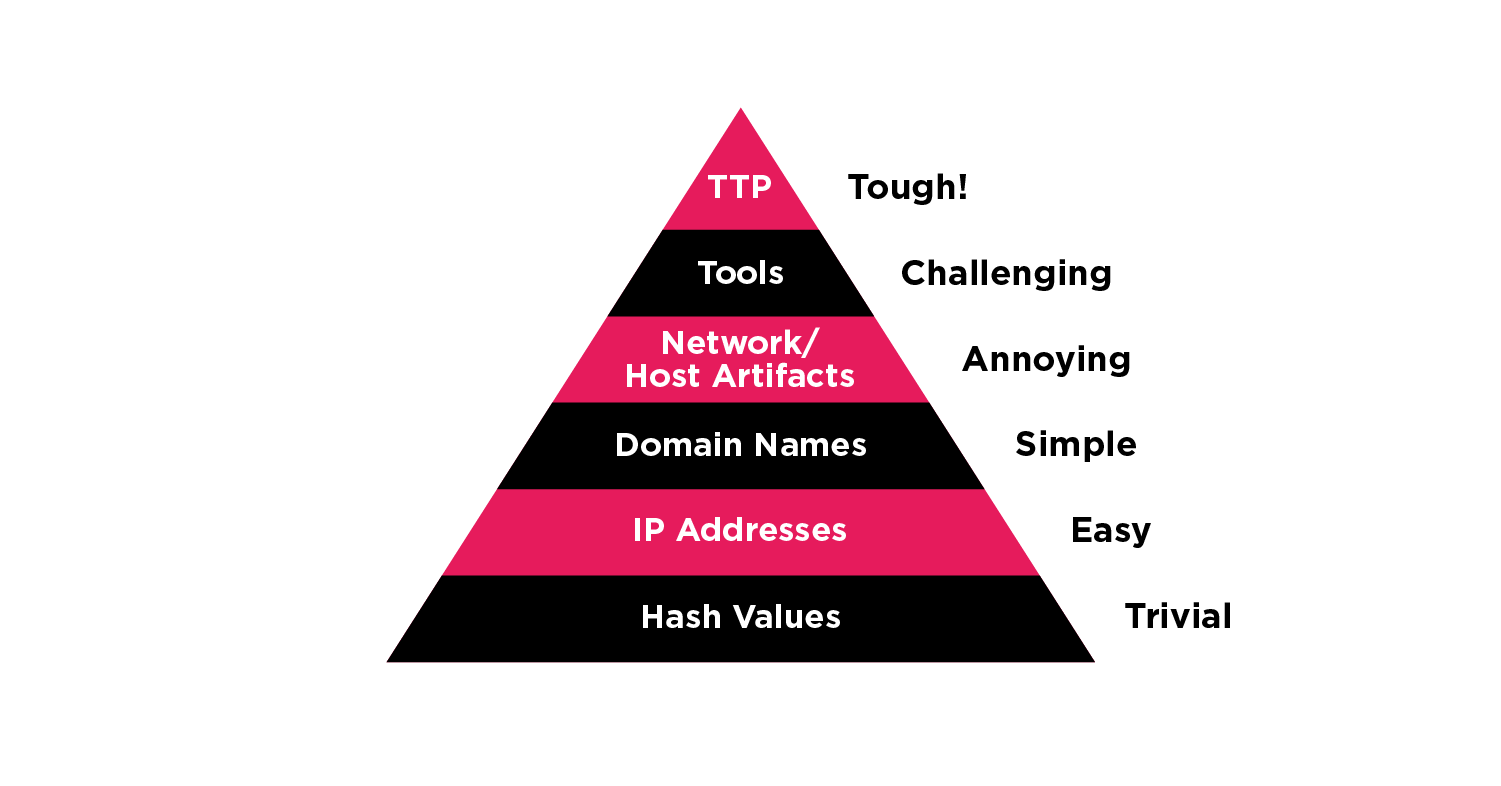
The best model illustrating how to make life harder for attackers is David Bianco's "Pyramid of Pain." As shown in Figure 1, the indicators on the lower end of the pyramid (e.g., hashes, IP addresses, and domain names) are relatively easy for the attacker to modify. The threat actor can quickly and easily change minimal elements of the attack pattern (e.g., a domain generation algorithm) and relaunch further attacks against your organization that are likely to bypass your SOC's latest IOC-based security mitigations. A TTP, such as relying on a specific protocol to exfiltrate stolen data, is more difficult for adversaries to change than simply changing the C2 server IP address.
From the above example, your SOC tracking and blocking exfiltration protocols force the adversary to use a different attack vector, such as a supply chain compromise, if they want to continue to attack your organization.
Implementing a new attack pattern imposes higher resource costs to retool and forces the adversary into new, unfamiliar territory where they are more liable to make errors. Any error an adversary makes is an opportunity for you to detect them sooner.
I don't have time to worry about TTPs
SOCs are inherently overloaded, and SOC teams are perpetually overworked. Changing the discussion from IOCs to TTPs at first may sound like a lot of extra work. It's tempting for your SOC analyst to say, "I don't care about what got us to this point; help me deal with the current fire I've got to extinguish." Persist. Moving beyond IOCs to TTPs has some inherent benefits for the SOC team:
Preventing future attacks
A focus on TTPs provides better context and detail SOC analysts can use to block further attacks. Every breach contained saves significant SOC resources. As discussed in our "Three Strategic Steps to a Threat-informed Defense (TiD)" post, one premise of a threat-informed defense is to research and validate the organization's ability to defend against specific attacks. TTPs enable you to rapidly model attacks with better context and detail. This additional context and detail arm your security teams with more information to make sure they cover the active threat and cut off the threat actor's key attack channels. For example, understanding that a threat actor using a particular strain of ransomware prefers remote desktop protocol (RDP) as their attack pivot vector provides you with directional insight. Instead of scrambling to mitigate ransomware as the attacker moves from system to system, blocking RDP access can stop them in their tracks, ultimately expelling them from your network.
Enabling threat hunting
Shifting to TTPs helps to direct threat hunting practices. Specifically, TTPs provide pivot points from specific attack elements by connecting the dots within attack patterns. By joining seemingly isolated events, TTPs facilitate hunting down otherwise undetected attacks. A neutralized threat vector is one fewer potential breach that your SOC and IR teams must deal with, ultimately freeing up strapped SOC and IR resources.
Making your SOC analyst's life easier
One of the most important benefits of shifting the focus to TTPs is improving information sharing between intelligence and security professionals. Your intelligence analysts and security experts may miscommunicate because they come from different perspectives. Your security team is 100 percent focused on protecting the organization right now. Your CTI team's focus is much broader: discovering what is going on now, reviewing what happened in the past, and projecting what might happen in the future. Through TTPs, both teams gain more attack context, enabling each to select the relevant information that supports their role and mission.
Pushing the CTI team to produce actionable intelligence
Just as the shift from IOCs to TTPs forces your SOC team to adjust its focus, it also puts significant pressure on your threat analyst team to produce easily consumable reports. These reports must empower your SOC and incident response (IR) teams with actionable insights and guidance that communicate common objectives. A key to developing actionable intelligence reports is finding the right balance between valuable data and supporting detail. Achieving this balance requires a threat intelligence management platform that makes it easy to generate reports that help non-CTI staff translate essential intelligence factors like confidence level and maliciousness into actionable information. As a CTI director at a global financial services organization told us, before implementing EclecticIQ Intelligence Center, no matter how hard his CTI team worked, the rest of the organization could not "take that extra step to leverage the intelligence. That step requires actionable intelligence."
Shifting to TTPs gives you time to breathe
The rat race created by continually trying to stop attacks with blocklists is exhausting and potentially catastrophic for your organization, since attackers quickly bypass the blocks. By moving up the Pyramid of Pain to focus on TTPs, your security and CTI teams change the game. This move requires changing both the focus of the threat intelligence and how it is developed and structured.
The beauty of shifting from "what" to "how" is that rather than being 100 percent reactive, your security team can take a breath and gain time to become proactive. Your SOC will still be under intense pressure to block active threats. However, by leveraging higher-level CTI that maps out specific TTPs in alignment with the kill chain, your SOC will not only be able to block existing threats intelligently and proactively but will also be better positioned to prevent future threats.
As we discuss in “Achieving Early Warning for Cyber Resilience,” shifting from "what" to "how" also positions your organization to play a more significant role in the broader threat intelligence community. Through collaboration and sharing, you can both help other organizations and leverage their CTI for a more robust defense.