In our last post, we outlined three steps to jumpstart the CTI lifecycle and align it with your threat intelligence platform (TIP) by focusing on people, process, and technology. We highlighted that high-performing CTI teams have a dedicated TIP and follow a disciplined CTI lifecycle. Their success rests on properly aligning their TIP, the CTI lifecycle, and threat feeds. Get this alignment right, and you're set for high-performing operations. If you get this wrong, you risk loading your TIP with trash data, causing analyst burnout and developing and disseminating low-confidence and inaccurate threat intelligence. In this blog, we explain why getting the correct feed alignment requires rethinking your feed selection and curation process.
The reality of threat intelligence feeds
Threat feeds are essential for a functional TIP. A TIP without threat intelligence data is like a car without any petrol. It's worthless to you. "Gassing up" your TIP requires connecting to a feed (e.g., open, commercial, community, or self-generated). Unfortunately, unlike your options at a typical petrol station, which offers just a few fuel grades, you can choose from hundreds of threat intelligence feeds.
Not only must you gas up your TIP before it can work, but you also must input high-quality fuel with the right octane level and detergents to keep the engine running smoothly. Otherwise, your TIP's performance will suffer dearly. As our clients tell us, their most significant challenges are sorting through all the possible threat data sources and ensuring that the data from those feeds is reliable.
"Garbage in/garbage out"
As one of our threat analysts often reminds his team, when it comes to threat feeds, "garbage in means garbage out." Trashy data (i.e., unreliable, old, inaccurate) negatively affects every stage of the CTI lifecycle (see Figure 1):
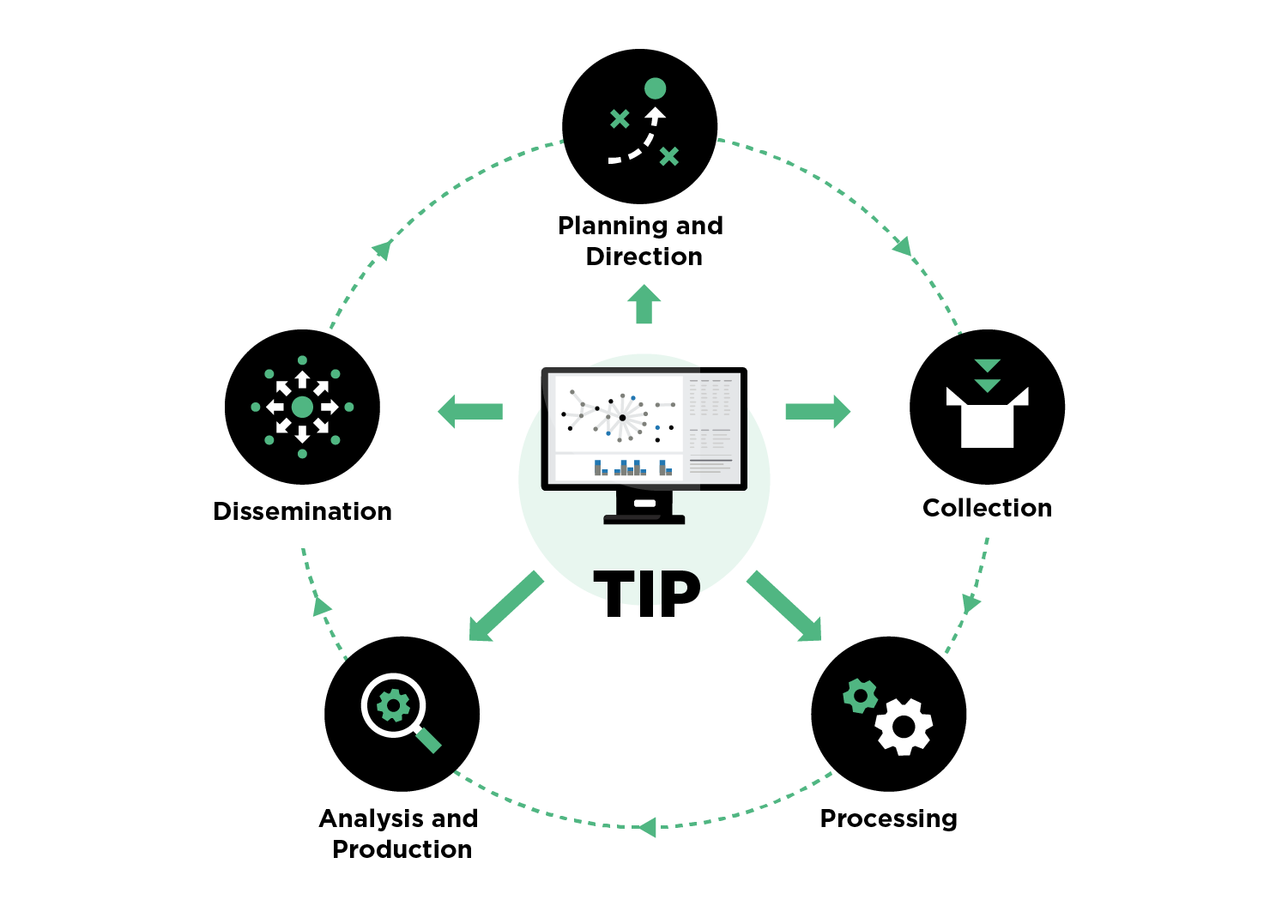 Figure 1 - CTI Lifecycle
Figure 1 - CTI Lifecycle
- Stage 1, Planning and Direction: Though planning and direction is largely an off-TIP exercise, bad data can lead to inaccurate assessments of the organization's risk profile and current threat landscape.
- Stage 2, Collection: TIPs have difficulty normalizing and deduplicating bad data. For example, they have a difficult time determining data reliability. This challenge results in ingestion of low-reliability data and potential rejection of high-reliability data.
- Stage 3, Processing: Analysts waste hours analyzing poor data. Often, it isn't until late in the analysis that they realize the data is unreliable or downright inaccurate.
- Stage 4, Analysis and Production: Poor-quality data that makes it past analysis becomes part of the production of the analyst team. This is a dangerous situation since other organizations expect this threat intelligence to be reliable and accurate.
- Stage 5, Dissemination: Finally, organizations downstream (e.g., the supply chain) receive poor-quality threat intelligence through the dissemination process.
The garbage-in-garbage-out problem leads to threat intelligence that isn't actionable. Worse, by providing a false sense of security, it might be misleading. You could miss active threats or waste resources by focusing on threats that aren't relevant.
Threat feed marketplace or potential garbage dump?
Our clients' garbage challenge has two components: feeds that do not effectively cover the threat landscape and the inability to manage feed reliability and quality. The root of these problems rests with the threat feed marketplaces provided by most major TIP vendors. These marketplaces serve as a central spot to select threat feeds. The upside of a marketplace is extensive choice. With one click, your analysts can subscribe to a new threat feed. The downsides are twofold. First, marketplaces rarely include boutique feed sources. Instead, they focus almost exclusively on mainstream and open source feeds. This limitation is a glaring coverage gap. As discussed below, boutique sources can be a cost-effective alternative to mainstream feeds for less mature organizations and can fill essential gaps in threat landscape coverage for more-mature organizations.
The second limitation of threat feed marketplaces is that only the mainstream feeds guarantee data quality and reliability. All other feeds require careful monitoring for source quality and reliability over time, not just at the time you select them. Your CTI analysts risk having a reliable feed become unreliable. Unfortunately, they will probably not realize this until after they've wasted valuable cycles investigating threats that are either nonexistent or irrelevant, on one hand, and, on the other, exposing the organization to risk by missing highly relevant threats.
Threat data sources
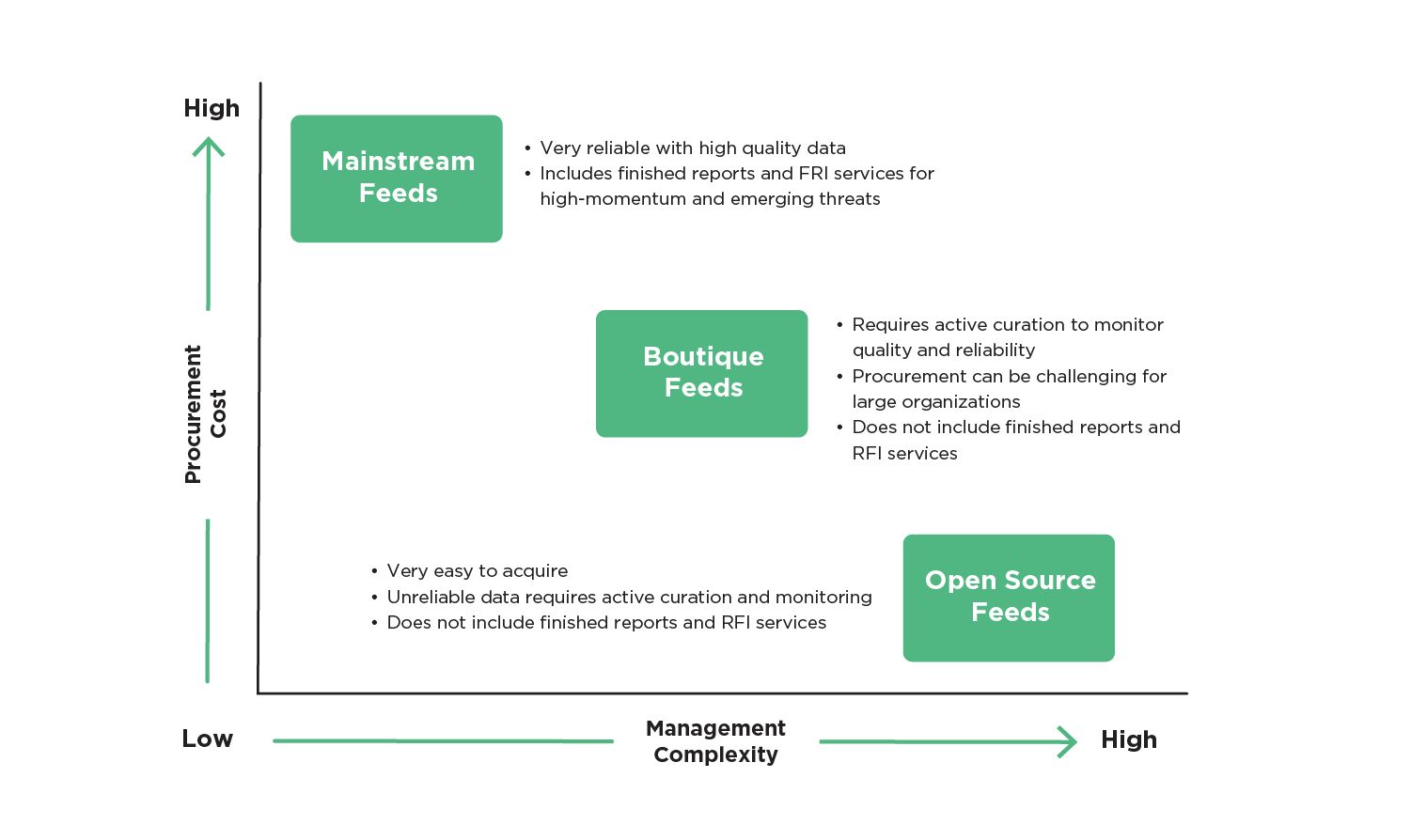 Figure 2 - Threat Feed Categories
Figure 2 - Threat Feed Categories
As noted above, there are three principal types of threat feeds: mainstream, boutique, and open source. Mainstream feeds are high-cost, closely managed feeds that provide reliable and high-quality data in addition to finished reports and request for information (RFI) services for high-momentum and emerging threats. Boutique feeds provide specialized threat data that focuses on the top threats (e.g., ransomware, phishing, denial of service) that organizations face on an ongoing basis. These feeds augment mainstream feed threat coverage and are much more affordable. However, unlike the mainstream feeds, boutique feeds are often challenging to find and procure because they are typically not in threat feed marketplaces. Open source feeds are low or no-cost sources of threat data. Though these feeds are extremely easy to find and include much of the threat landscape coverage of the boutique and mainstream feeds, they are notoriously unpredictable, requiring extremely close monitoring for data reliability and quality. Unlike mainstream feeds, neither boutique nor open source feeds include finished reports and RFI services.
A different approach to threat feed marketplaces
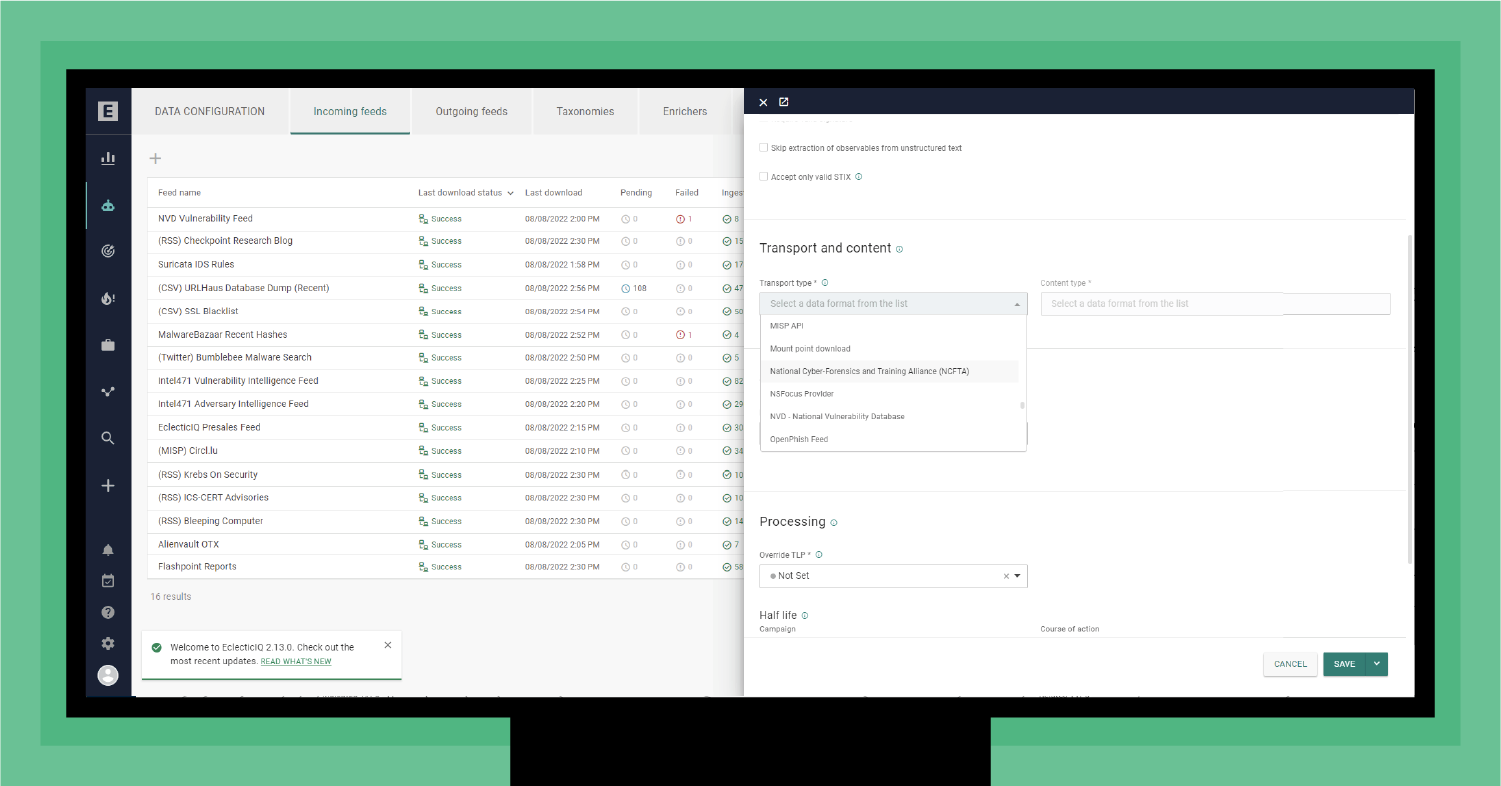 Figure 3 - Selecting a feed integration
Figure 3 - Selecting a feed integration
At EclecticIQ, we take a comprehensive approach by providing our clients with all three types of feeds while addressing the garbage-in/garbage-out challenge. We provide our clients with three feed integration options. First, like a feed marketplace, we offer convenient, direct integrations with over 75 feed partners from the EclecticIQ intelligence Center feed integration tab. As shown in Figure 3, your operators never need to leave their TIP workflow.
Adding a new feed is as simple as selecting the feed provider from the transport and content drop-down list. This list includes sources our clients use daily from the three categories (mainstream, boutique, and open source). The list also provides integrations for any feed using Structured Threat Intelligence eXchange (STIX) and Trusted Automated eXchange of Indicator Information (TAXII).
The second option for our clients is our Curated Feeds. We recognize that organizations (including yours) face a set of top threats, including exploits, polymorphic malware, phishing, and ransomware. To address these threats, your CTI team must populate its TIP with reliable, high-confidence, consumable, and actionable threat data.
Plus, one size does not fit all. Organizations just starting their CTI practice may not be ready to procure expensive mainstream threat feeds, and more-mature organizations look for feed variety to increase their threat landscape visibility.
EclecticIQ Curated Feeds service covers top threats with a combination of open and commercial sources. These feeds are optimized for EclecticIQ Intelligence Center and constantly monitored by the EclecticIQ Threat Research Team for data quality and reliability. The Open Sources Feed comes with EclecticIQ Intelligence Center at no additional cost. The Commercial Sources Feed is a cost-effective add-on with original data from advanced boutique threat data vendors and EclecticIQ threat intelligence. It uses machine learning to process data from more than 550 million sensors, sandboxes, honeypots, net analyzers, web crawlers, traps, monitored botnets, dark websites, and bulletproof hosting providers.
As mentioned above, only mainstream feeds include finished reports and RFI services for emerging or high-momentum threats. As a bonus, our Commercial Sources Feed contains strategic and tactical reports from our EclecticIQ threat research team. These reports provide actionable guidance, directly integrated into EclecticIQ Intelligence Center, on critical and emerging threats, threat actors, and their tactics, techniques, and procedures (TTPs).
The third option we offer is an extensible REST API that allows your analysts to programmatically interact with an EclecticIQ Intelligence Center instance. The API supports direct integration with any data feed, giving your CTI analysts the flexibility to ingest any source data in virtually any format.
 Figure 4 - EcleccticIQ API (developers.eclecticiq.com)
Figure 4 - EcleccticIQ API (developers.eclecticiq.com)
The API gives you complete flexibility to integrate any feed not already preset in EclecticIQ Intelligence Center or available through our Curated Feeds service.
Maximal feed value requires optimization
As a huge plus for your CTI team, the EclecticIQ Curated Feeds service is optimized for EclecticIQ Intelligence Center. Optimization is a universal challenge for TIPs, given that most available feeds are not standard STIX/TAXII). Because of this, every feed you integrate with your TIP requires some translation to ensure the feed data matches your TIP's data model.
Optimization is a straightforward process necessary for all feeds, though it's time consuming for your analysts. For example, a malware feed might have a "Malware_malpedia" attribute. The equivalent attribute in the EclecticIQ Intelligence Center data model is "reference." Similarly, the feed might have a "reporter" attribute that maps to the EclecticIQ "producer" attribute.
The upside of optimizing feeds is taking advantage of your TIP's ability to accurately align threat data from multiple feeds to significantly reduce false positives and help your analyst team prioritize threat intelligence.
Gold dust in, gold nuggets out
The beauty of having and optimizing the right threat feeds is support for each stage of your CTI lifecycle. Rather than pulling in the garbage, you pull in gold dust, so your threat intelligence becomes gold nuggets for your organization.
- Your TIP normalizes and deduplicates your threat data across multiple feeds. Optimizing your feeds ensures that high-confidence threat data is quickly available for your analysts, while your TIP automatically deprioritizes low-confidence data.
- Your analysts' productivity increases exponentially with high-confidence data so they can prioritize analyses and focus on the most pressing threats quickly.
- With high-confidence and high-reliability data, the reports your analysts generate – or pass on – are actionable, reliable, and consumable for your stakeholders.
- Finally, organizations downstream (e.g., the supply chain) receive high-quality threat intelligence through the dissemination process.
Conclusion
Together, our preconfigured feed integrations, the EclecticIQ API, and the EclecticIQ Curated Feeds eliminate the need for a threat feed marketplace. Your analysts get the flexibility they need to ingest any feed and a preconfigured set of feeds that cover the bulk of your threat landscape. This approach sets your CTI team up for high-performing operations, supports a robust CTI lifecycle, and eliminates the garbage-in/garbage-out threat feed challenge.