Introduction
To paraphrase a classic war protest song, "CTI? Huh! What is it good for? Huh! Absolutely nothing! Say it again, y'all!"
Though this sounds crazy, many organizations get surprisingly little value from their cyber threat intelligence (CTI). To underscore this point, only 41% of participants in a Ponemon study rated their use of threat intelligence as "highly effective."1
We know that CTI, itself, is not worthless. In another Ponemon study, 74% of respondents experiencing a breach stated that timely and accurate threat intelligence could have "prevented or mitigated the consequences of the attack."2 The operative words here are "could have." Unfortunately, most organizations cannot extract value from their CTI in time to prevent or mitigate a breach.
There is hope. Nearly three-quarters of the organizations Ponemon considers "high-performing" CTI teams rate their use of threat intelligence as highly effective.3 Our interpretation of this statistic is that these teams are highly effective because their CTI is actionable (the theme for this blog series!).
So, how do these CTI teams extract value from their CTI and make it actionable? One key factor is having a dedicated threat intelligence platform (TIP). However, a dedicated TIP alone is not enough.
A dedicated TIP?
There is a clear relationship between having a dedicated TIP and being a high-performing CTI organization. Ponemon found that 69% of respondents from high-performing threat intelligence organizations have a dedicated TIP.4
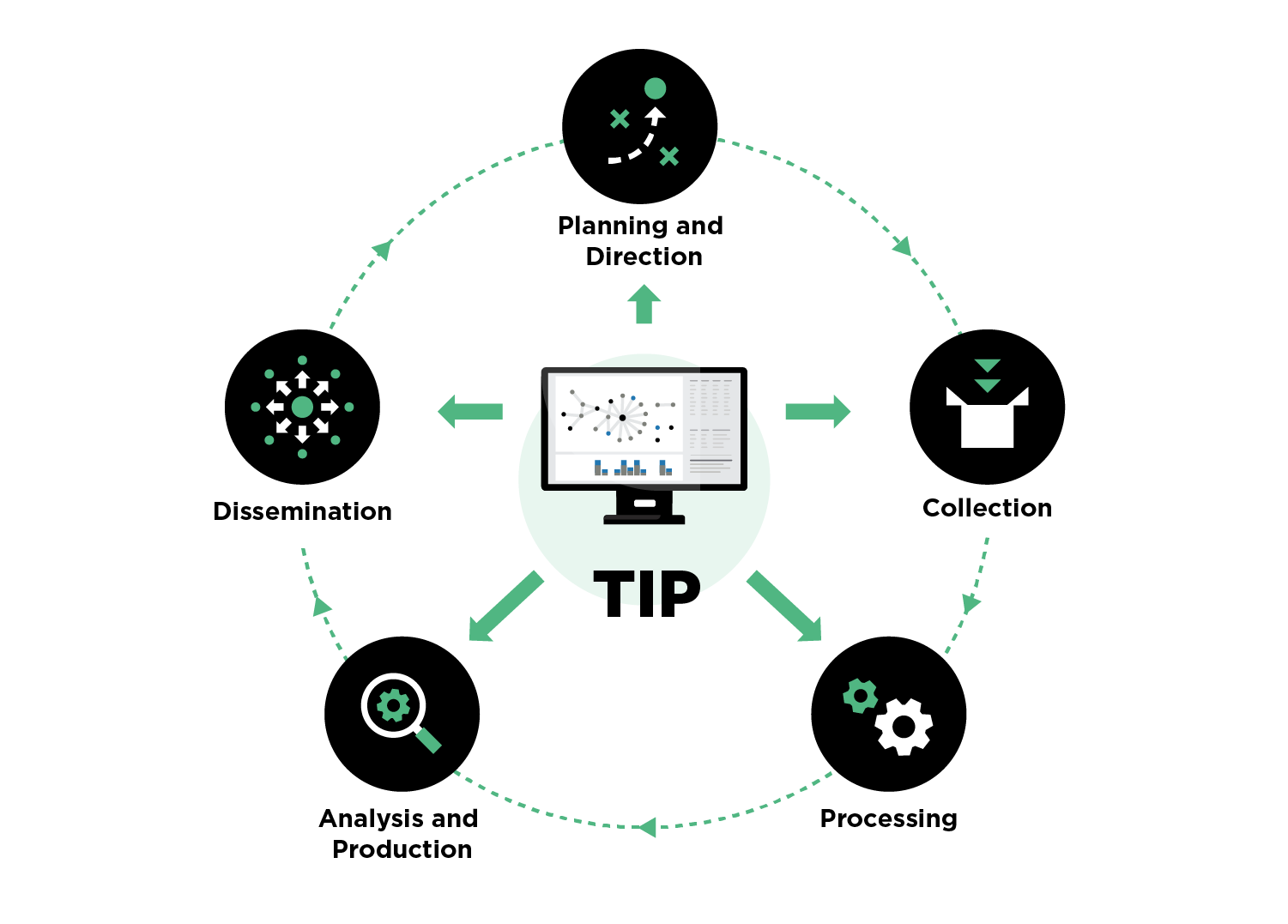
Figure 1 - TIP Lifecycle Support
As a TIP provider, we could wrap up this blog by saying, "Go buy our TIP now!" However, we must not confuse correlation with causation. Implementing a dedicated TIP contributes to actionable CTI but doesn't guarantee it.
Accelerating the CTI lifecycle
Based on working with some of the most targeted organizations in the world, we find that high-performing CTI teams implement a dedicated TIP not as an end in itself but in support of a disciplined CTI lifecycle.
As shown in Figure 1, the CTI lifecycle typically consists of five stages. Though a detailed discussion is beyond the scope of this blog, for a real-world use case, please read how our threat intelligence analysts followed this lifecycle to track threats throughout the COVID-19 pandemic. Read our white paper Tradecraft of a Successful Threat Investigation.
A dedicated TIP can accelerate moving through the lifecycle stages:
Planning and Direction
During this stage, the CTI team works with the rest of the organization to establish primary intelligence requirements (PIRs). PIRs direct the CTI team throughout the lifecycle and set up the guardrails that bind the scope of the CTI program. A TIP can provide the evidence your CTI team needs to track the PIRs and help your CTI analysts automate the workflows for each lifecycle stage.
Collection and Processing
Successful collection and processing involve ingesting, normalizing, and prioritizing millions of indicators, observables, and reports. A TIP with the processing horsepower to collect and enrich a continuous flow of threat data, plus a rules-based tagging engine, can automatically process and prioritize this data. A TIP with a database model that seamlessly handles structured and unstructured data formats can significantly reduce analyst workload at this stage of the lifecycle by offloading the manual task of normalizing threat data.
Analysis and Production
Analysis and production are the activities on which CTI analysts spend most of their time. A TIP with an analyst workbench, a rules engine for automated discovery, and an extensive graph for investigations and analysis can significantly reduce investigation times. The TIP can support collaboration between internal and external stakeholders for extensive joint threat investigations and analysis for report production.
Dissemination and Collaboration
As the last lifecycle stage, dissemination and collaboration provide a window into CTI operations for the rest of the organization. The TIP can help analysts ensure that each intelligence report's format, tone, and technical detail match the target audience's needs and expectations. Further, the TIP can support the effective delivery of reports to your security organization, structured threat intelligence to your information sharing analysis center (ISAC), and threat data to your security controls while protecting confidentiality, integrity, and privacy.
The hard reality facing an operational CTI team
Just as a fully operational TIP can speed you through the lifecycle, a poorly implemented TIP can bring you to a screeching halt. To this point, we see even mature CTI teams struggle to achieve a successful CTI lifecycle model because they do not adequately stand up their TIP in a way that tightly aligns with their lifecycle processes.
This situation is primarily driven by the cybersecurity skills shortage. Frequently quoted as the top concern of CISOs, the deficit is particularly challenging for CTI teams. It creates challenges that can torpedo your CTI team's ability to implement a successful lifecycle and collect, analyze, develop, and disseminate actionable CTI (see Table 1).
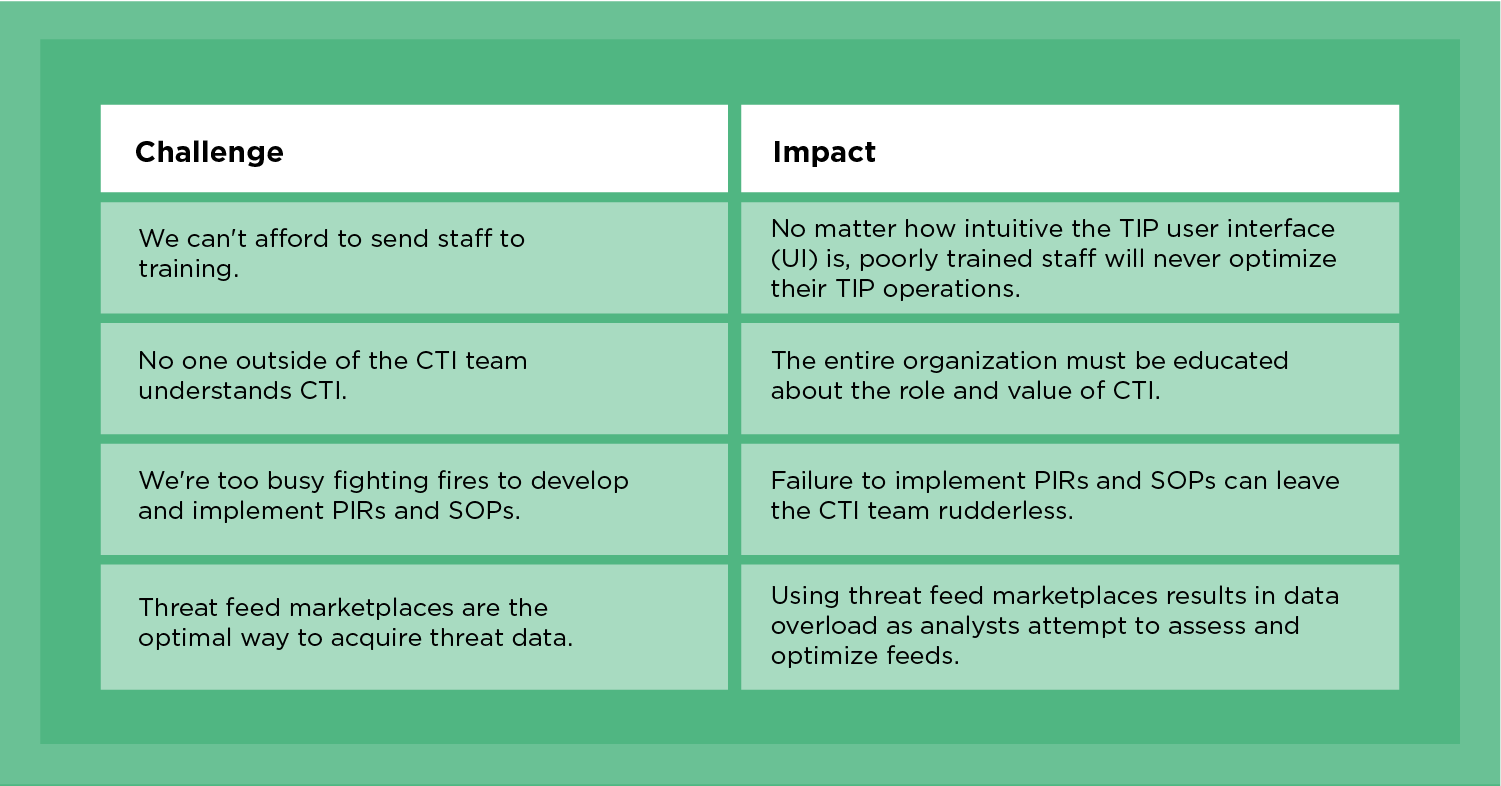 Table 1 - Challenges in Aligning the TIP to the CTI Lifecycle
Table 1 - Challenges in Aligning the TIP to the CTI Lifecycle
A pragmatic approach
The cybersecurity skills shortage is not going away. Because of this, you must be creative in working around the above challenges to jumpstart your CTI lifecycle and TIP alignment. We recommend a pragmatic approach focusing on your people, processes, and technology:
-
People: jumpstart organizational CTI knowledge
CTI provides value to every team in your organization. In our experience, managing colleagues' expectations regarding threat intelligence is challenging. Quite often, groups outside the CTI organization misunderstand what CTI is, how the TIP helps to produce it, and how best to use it. For example, a global bank client of EclecticIQ found that executives did not understand that threat intelligence delivers attack likelihood and possible impacts, not guarantees. Without realistic expectations and a common level of understanding, your stakeholders will not properly use your CTI; worse, they may misinterpret it, resulting in poor decisions.
Staffing challenges negatively impact the effectiveness of the CTI lifecycle. This factor is especially true for analysis and production, the most analyst-intense stages. Because each TIP solution provides a unique UI requiring specialized training, CTI analyst turnover results in ebbs and flows in your team's ability to maximize your TIP for these critical functions.
Training must be focused, pragmatic, and structured to help you align your TIP to your CTI program. The optimal situation is a short, on-site engagement and a TIP-specific program that allow students to learn on an instance of their TIP without leaving their workplace. The days of traveling to a weeklong training session at a vendor's location are over.
We recommend implementing training across the organization to instill a common, baseline understanding of CTI and the TIP's role in collecting, processing, and disseminating it. This type of training will help jumpstart your organizational CTI knowledge.
-
Processes: jumpstart the CTI lifecycle by establishing SOPs and PIRs
Few teams have the formal training and experience necessary to develop and implement SOPs and PIRs. Often, organizations create PIRs that are too broad, which prevents the CTI team from developing actionable intelligence. When the PIRs are too generic, the CTI team cannot leverage the TIP to help prioritize and analyze the data.
We advise hiring specialized consultants to help your organization establish SOPs and PIRs that meet your unique needs. The consultants must be familiar with your specific TIP so they can help your team implement the SOPs and PIRs. Otherwise, your team will spend many hours translating generic consulting advice into actionable TIP practices.
-
Technology: Jumpstart TIP operations with feed quality and management
A critical factor in jumpstarting TIP operations is recognizing that, despite TIP automation and machine learning, analysts must still manually process incoming feeds – which can number in the hundreds. Staff shortages and a lack of CTI analysis skills will limit your ability to optimize these feeds. We find that many organizations turn them off because the amount of work needed to maximize the data coming into the TIP overwhelms understaffed CTI teams. To address this challenge, we recommend finding services that help you select and optimize feeds for your TIP. As discussed in our next post, choosing the right feeds that focus on top threats and optimizing them for your TIP significantly reduce your analysts' manual workload while greatly improving their performance.
Conclusion
By focusing on your people, processes, and technology to jumpstart your TIP operations in support of a robust CTI lifecycle, you will significantly improve the effectiveness of your CTI by making it actionable. In our next post, we'll illustrate how EclecticIQ Curated Feeds solution helps our clients achieve this goal.