Though there are broadly adopted capability maturity models for other areas of IT (e.g., CMMI, COBIT, NHS Infrastructure Maturity Model), a widely accepted CTI capability maturity model has not yet emerged. Some excellent work is ongoing at the TUDelft Cyber Threat Intelligence Lab [1] and within ENISA [2,3], but no de facto model exists.
The EclecticIQ CTI Capability Maturity Model (CTI - CMM) for organizational intelligence is inspired by the great work of Robert M. Clark (author of "Intelligence Analysis: A Target-Centric Approach"), CPNI/CERT- UK's publications on threat intelligence, and the iSIGHT Partners Threat Intelligence Maturity Model.
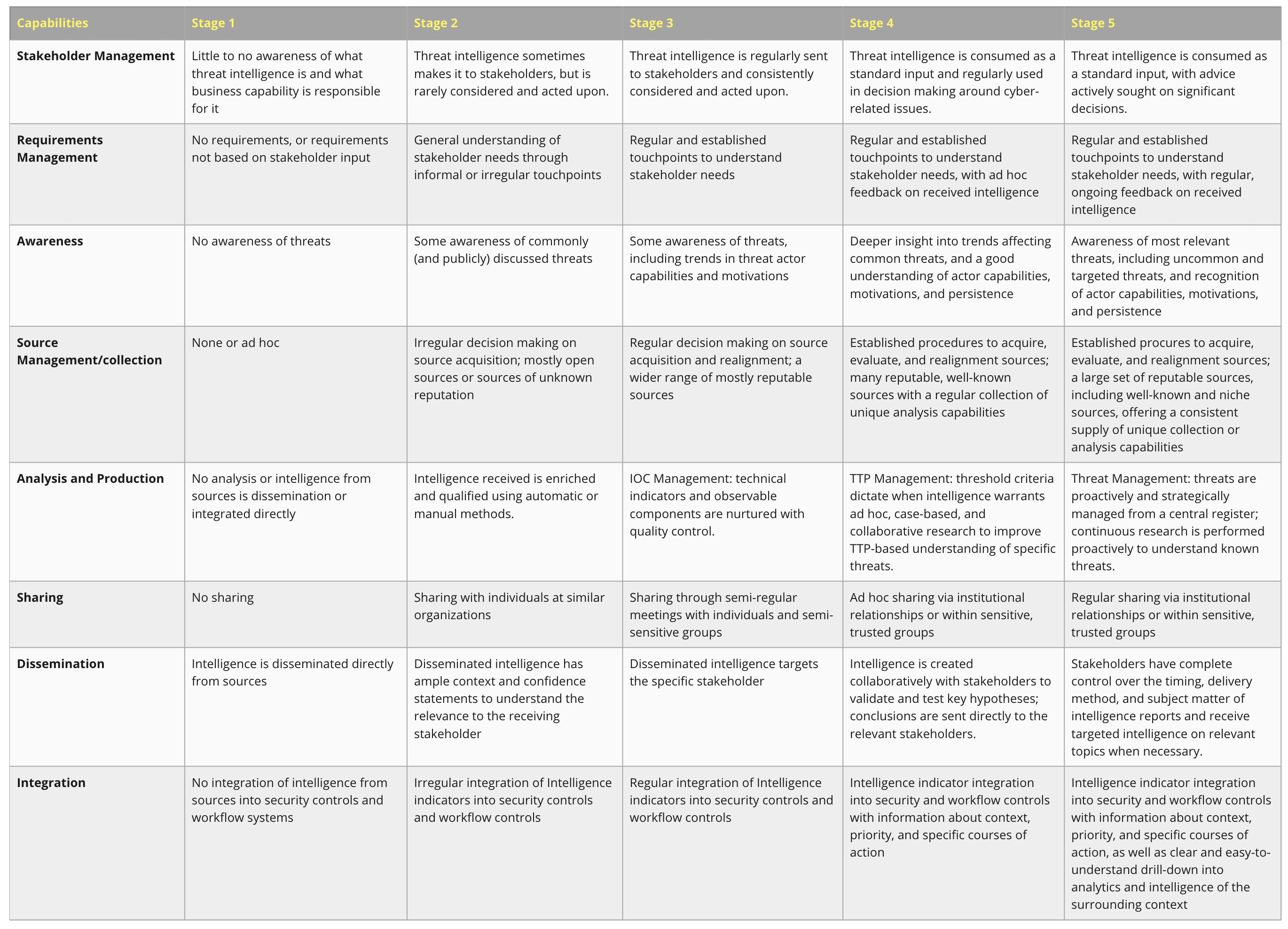
Like other capability maturity models (e.g., CMMI), the CTI - CMM establishes a five-level (stage) assessment scale that measures your maturity across eight distinct CTI capabilities.
Overall, the model covers three broad areas (See Figure 1):
Figure 1 - Three broad areas to measure CTI maturity
-
Alignment with business and threat reality: Measures how well your investments in threat intelligence reflect business needs, resource constraints, and the threat landscape.
-
Ability to understand cyber threats: Measures how well your analytic capabilities allow your threat intelligence teams to understand cyber threats in the context of stakeholder needs. Essential functions include qualifying technical indicators and strategically tracking critical cyber threats facing similar organizations and industries.
-
Ability to control/take action on cyber threats: Measures the capability of your organization to handle, act on, and contain threats. Key functions include collecting relevant technical indicators, instrumenting detection and prevention systems, and engaging business stakeholders in how the changing threat landscape drives appropriate investment and business decisions.
Five stages of CTI maturity
Table 1 lists the five stages of maturity for each of the eight capabilities making up the CTI - CMM. Each stage builds on the previous one. With this approach, you gain the big picture (e.g., going from threat ignorance to full awareness) and learn how to move incrementally from one stage to the next (e.g., shifting from non-existent to basic awareness by tracking publicly discussed threats).
Table 1 - CTI maturity levels (click the image to zoom in)
Yes, we’ve just presented a ton of information. We realize that mapping eight capabilities across three practice pillars and five maturity stages sounds like a lot of moving points. However, as discussed in our next blog, turning this information into something actionable is surprisingly straightforward.
References
[1] https://ctim.eu/
[2] https://www.enisa.europa.eu/news/enisa-news/csirts-maturity-moving-to-the-next-level