In our last post, we outlined challenges to operationalizing CTI and making it actionable, including threat adversaries are becoming cleverer, the rapidly expanding attack surface increases your vulnerability, siloed operations are driving gaps in coverage, and information overload is making detecting advanced threats harder.
Four steps can overcome four challenges
Here are four concrete steps that you can take with EclecticIQ Intelligence Center to up your game by making CTI actionable. We like to characterize these steps as smarten up, open up, tighten up, and power up.
Step 1: Leverage threat intelligence expertise to smarten up your SOC
As threat adversaries improve their TTPs, the onus is on you to keep up. Unfortunately, most organizations are understaffed with CTI expertise in short supply. As we’ll discuss in an upcoming post, one approach is leveraging our robust CTI training to upskill team members. However, there’s also something you can do immediately to gain an advantage against adversaries. You can smarten up your SOC by taking advantage of EclecticIQ’s world-class Threat Research Team.
Our team of CTI analysts uses EclecticIQ Intelligence Center to help them stay on top of the threat landscape. Using their instance of EclecticIQ Intelligence Center, our customers leverage the team’s knowledge and expertise in multiple ways, two of which are Knowledge Packs and Curated Feeds.
EclecticIQ Knowledge Packs
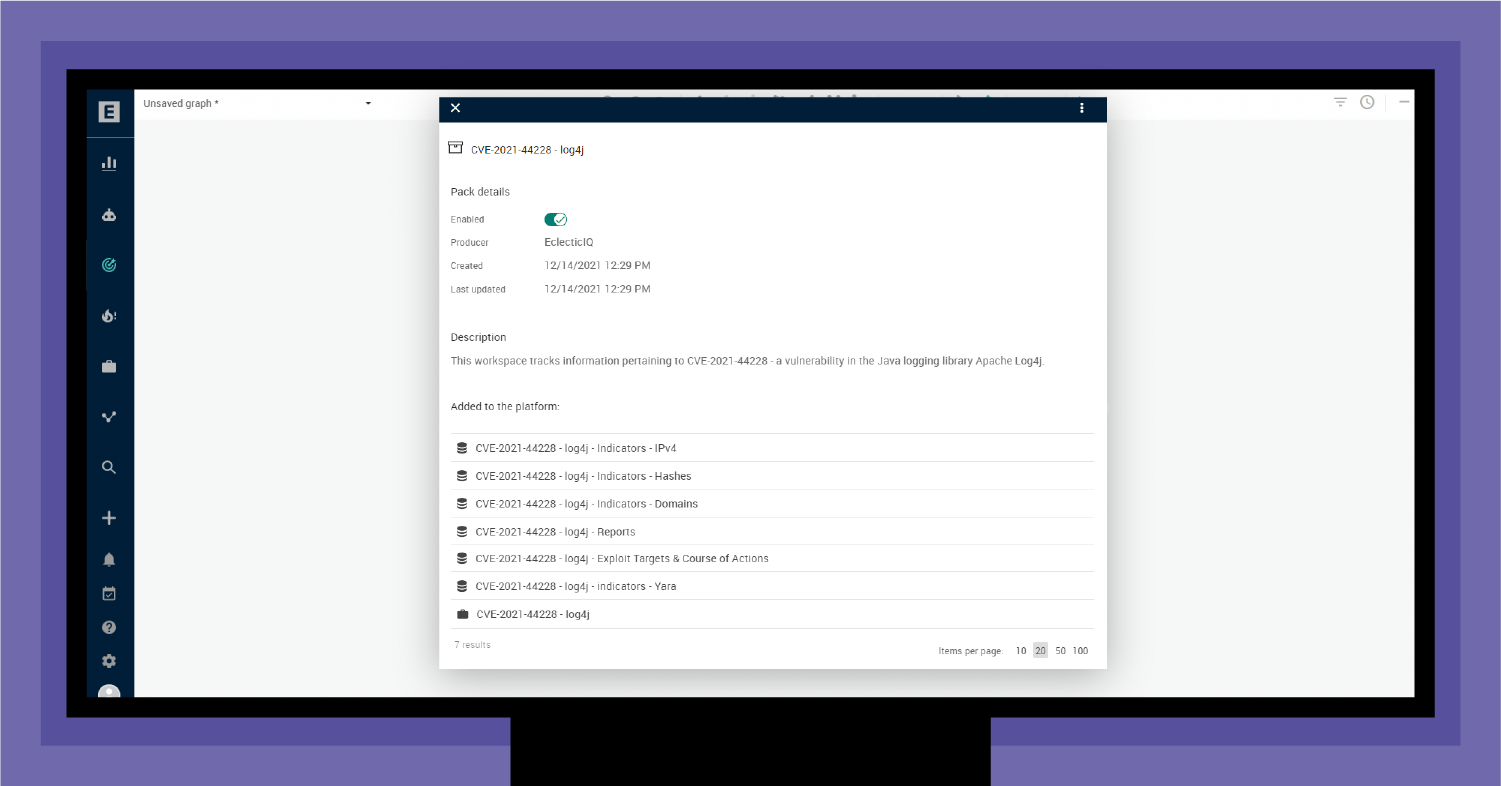
A Knowledge Pack includes preconfigured rules and datasets on specific topics that Intelligence Center customers can download. For example, shortly after the announcement of the Log4j vulnerability (CVE-2021-44228), the EclecticIQ Threat Research Team created a Knowledge Pack for Log4J. Other Knowledge Packs focus on specific malware or global events that trigger malicious activity, such as the Russian war on Ukraine. Each Knowledge Pack automatically organizes the relevant data from EclecticIQ Intelligence Center, including:
- Indicators – IPv4, hashes, domains
- Reports
- Explicit targets & courses of action
- YARA formatted indicator lists for automated processing
When you click on the Knowledge Pack of interest, EclecticIQ Intelligence Center generates a dedicated workspace on the fly. For example, as shown in Figure 1, the Log4j (CVE-2021-44228) Knowledge Pack lets you instantly start tracking relevant, timely threats without spending any time or effort manually configuring the workspace.
Knowledge Packs smarten up your SOC by allowing your team to start monitoring and taking action right away, regardless of their level of CTI expertise.
EclecticIQ Curated Feeds
The overwhelming number of open source and commercial threat feeds is a side effect of the rapidly expanding threat landscape and growing attack surface. Customers tell us that threat feed marketplaces cause data overload and analyst burnout. Analysts waste hours processing, structuring, and tagging sub-optimal data full of false positives. Worse, they spend months trying out various feeds, dealing with procurement, and wasting time and budget culling less-valuable feeds.
As a result, many organizations ignore most of the data from their threat feeds. Not only is this nonproductive, but it also puts the organization at significant risk of missing relevant threat intelligence.
To overcome this challenge, EclecticIQ offers two threat data feeds curated for primary threats and optimized for EclecticIQ Intelligence Center. These feeds can smarten up your SOC with highly relevant data:
- The Open Sources Feed, which comes with EclecticIQ Intelligence Center, includes an evolving set of what our analysts believe to be the most accurate and relevant open-source intelligence feeds.
- The Commercial Sources Feed is an add-on to EclecticIQ Intelligence Center that includes original data from unique boutique threat data vendors, as well as threat intelligence reports, Rapid Alerts, and Threat Overviews from the EclecticIQ Threat Research Team. The Commercial Sources Feed is cost-effective, providing you access to multiple threat data vendors in a single procurement. Data from this feed is derived with machine learning (ML) from more than 550 million sensors, sandboxes, honeypots, net analyzers, web crawlers, traps, monitored botnets, and the dark web.
With these feeds, your team receives relevant, continually updated pre-tagged and optimized data for EclecticIQ Intelligence Center. They provide data not found elsewhere. For example, we recently announced the addition of unique “bulletproof hosting” data in our Commercial Sources Feed to help customers identify cybercriminal infrastructure.
Step 2: Apply open standards like STIX 2.1 to open up intelligence sharing and collaboration
Successful security and risk management is a team sport—the more collaborative the environment, the greater the chance that collective knowledge and expertise will outmaneuver adversaries’ TTPs. An essential aspect of collaboration and sharing is using open standards like Structured Threat Information eXpression (STIX). STIX 2.1 is the most current approach for automated intelligence sharing. It automates the exchange of observables and their relationships with granularity and context. EclecticIQ Intelligence Center provides interoperability with STIX 2.1 by delivering the seamless ingestion and dissemination of STIX 2.1 data.
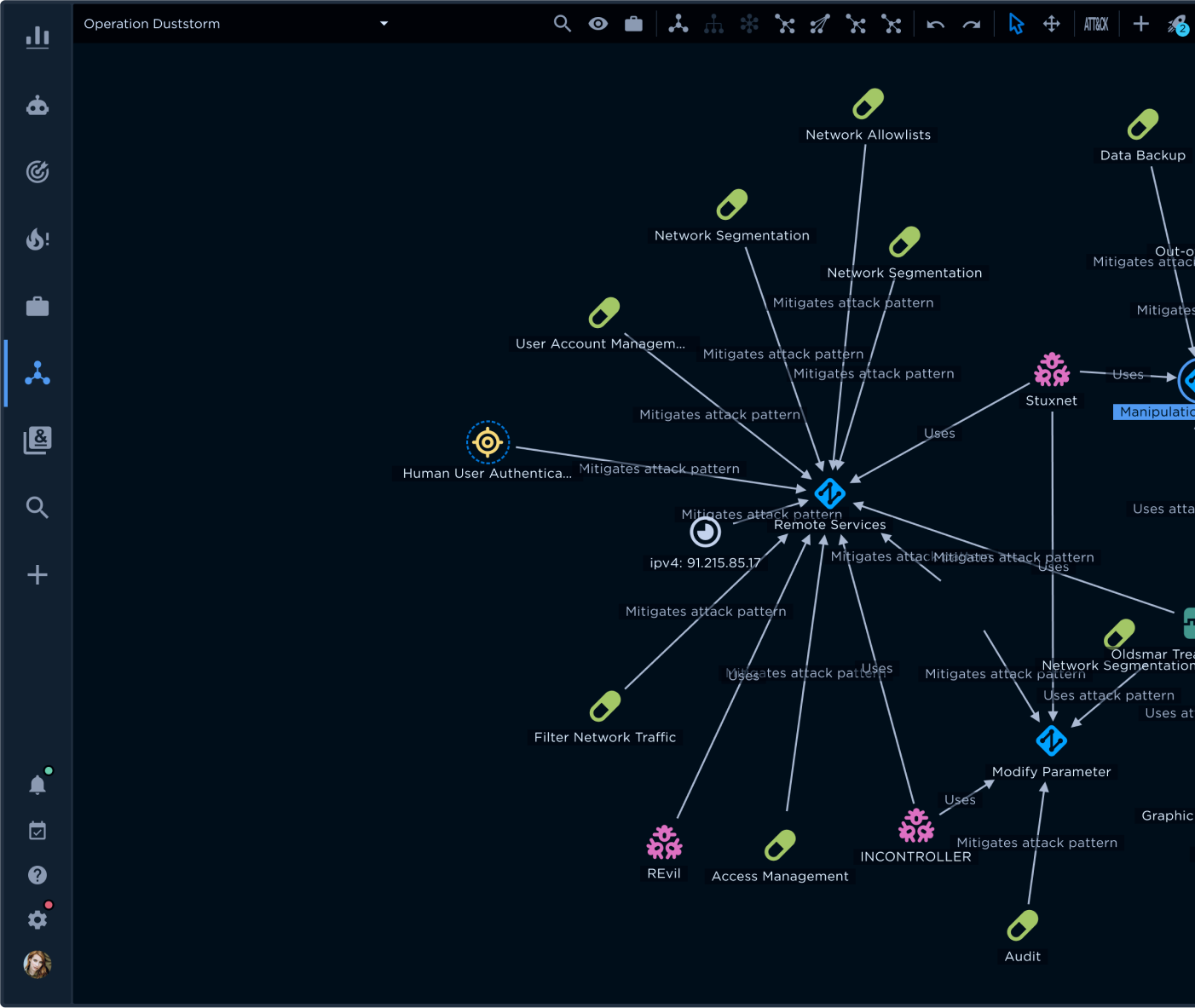
To achieve the full potential of STIX 2.1, EclecticIQ Intelligence Center empowers your analysts to turn STIX Domain Objects (SDOs), STIX Cyber Observable Objects (SCOs), and STIX Relationship Objects (SROs) into insights they can use for actionable intelligence. For example, an attack pattern or malware signature may indicate a potential attack. EclecticIQ Intelligence Center builds on related information by enabling CTI analysts to make crucial connections, automatically create graph charts, and enrich data to establish the TTPs behind the attack quickly. These capabilities empower your team to transition from indicator-driven insights to TTP-driven insights. This approach accounts for changes in adversary methodologies to keep your CTI actionable as you keep up with evolving threats.
The most highly targeted organizations in the world trust EclecticIQ Intelligence Center to balance interoperability with extensibility and analytical depth. They rely on EclecticIQ Intelligence Center for the scalability necessary to process millions of data points daily from STIX and non-STIX sources. Analysts get a contextual source of truth from these data points, which extends beyond STIX and enables them to conduct deep investigations into the TTPs of sophisticated threat actors. At the same time, EclecticIQ Intelligence Center opens up your threat intelligence sharing and collaboration as it delivers effortless STIX (and non-STIX) data interchange and seamless interoperability with STIX 2.1 preferred feeds and security controls.
Step 3: Implement an API-driven architecture to tighten up gaps in coverage
The expanding threat landscape and growing attack surface require you to manage an ever-increasing volume of threat data while integrating your security tool stack to close gaps in coverage. These gaps typically arise from siloed operations and point solutions that do not readily interact.
To help you close these coverage gaps in your security stack, EclecticIQ Intelligence Center delivers an extensible API useful to CTI analysts, not just application developers. This API offers the following benefits:
1) A consistent view
We make it easy for your SOC analysts to integrate intelligence from EclecticIQ Intelligence Center with your SIEM and SOAR platforms, the bread-and-butter tools of the SOC. With this two-way API, SOC teams can send and receive sightings and observables between the SIEM or SOAR and EclecticIQ Intelligence Center without jumping away from their console of choice.
2) Integrated identity management
EclecticIQ Intelligence Center supports access from across your organization (e.g., SOC, CTI, Risk Management, Incident Response, and Vulnerability Management). The API seamlessly integrates with your identity store (e.g., Active Directory) to automatically keep user access rights current.
3) Synchronization between EclecticIQ Intelligence Center and the security stack
For example, via the API, your CTI analysts can develop custom scripts to fetch taxonomies from other data sources and align them with EclecticIQ Intelligence Center and a unified data model.
For CTI analysts, the EclecticIQ API automates bulk actions on massive amounts of data. Analysts can write custom scripts quickly (with the help of example content on the dev hub) to efficiently perform automated actions (and save a lot of manual work through the UI).
If your developers are new to CTI, our Threat Research Team’s experts make available a broad base of example content and posts that explain core CTI concepts. This content includes programmatic guides to help onboard non-CTI teams. It lives in the EclecticIQ Developer Portal on one easy-to-navigate, self-service website.
The bottom line is the EclecticIQ API, and the content and community we’ve built around it, help you to tighten up potentially dangerous gaps in coverage among security tools.

Step 4: Implement a threat intelligence platform to power up your CTI analysts
Despite all the media focus on AI and ML as the saviors of CTI, our clients find that a successful CTI practice relies on a skilled analyst team that follows a disciplined lifecycle model. They require a threat intelligence platform like EclecticIQ Intelligence Center to accomplish the following:
Identify the most critical threats faster through contextual intelligence and automated threat data collection and processing
The EclecticIQ Intelligence Center Analyst Workbench supports the entire investigation process, starting with augmenting existing intelligence by quickly adding or editing STIX-compatible data from within the workbench. Your analysts can pull content directly from the web while browsing threat intelligence content with an integrated browser extension.
Accelerate investigations of sophisticated threats through team collaboration and workflow automation
With EclecticIQ Intelligence Center, your analysts conduct deep threat investigations using advanced search queries, intuitive graphical link analysis, and support for leading CTI frameworks, standards, and libraries. These capabilities help your analysts identify sophisticated TTPs.
Improve detection, hunting, and response with curation and granular integration of intelligence and threat detection content into third-party security controls (e.g., SIEM, SOAR, firewalls)
EclecticIQ Intelligence Center provides a broad base of connectors and apps to seamlessly integrate with the entire security infrastructure.
Disseminate actionable intelligence at machine speed – with privacy and governance – to enhance threat detection, industry collaboration, and decision making
EclecticIQ Intelligence Center facilitates engagement with your executives and third-party collaborative communities (e.g., ISACs, agencies, industry partners) while controlling the sensitive information your analysts share. Or you can build your collaborative network in a hub-and-spoke, mesh, or combined architecture while retaining complete privacy to ensure role-based access control (RBAC).