Intelligence Center: The AI-embedded Threat Intelligence Platform
What our Threat Intelligence Platform (TIP) can do
-
1. Direction & planning
Gain clarity and set the right intelligence priorities.Our platform helps you define and capture your Intelligence Requirements (IRs) in one place with Intelligence Compass. Using AI-driven and keyword-based mapping, it aligns threat information with your business context—ensuring your team stays focused on what matters most. You can assign tasks, track progress, and ensure no critical piece of intelligence slips through the cracks. Custom, role-specific dashboards let you visualize and track key metrics and threats, while our dynamic Observable Risk Score feature helps quickly identify and prioritize the most critical risks. Automated discovery rules and real-time alerts keep you ahead of emerging threats, so you can respond quickly while staying aligned with your core objectives.
-
2. Data collection
Bring all your intelligence into one view, no matter where it comes from.Learn more2. Data collection
Bring all your intelligence into one view, no matter where it comes from.We make it easy to integrate and normalize data from multiple sources and formats. With automated feeds, custom uploads, flexible integrations, and tools like Threat Scout, you can gather and organize data seamlessly. The platform automatically normalizes everything into STIX 2.1 and EIQ-JSON formats, providing a consistent foundation for the next steps in your analysis. No more messy, inconsistent data.
-
3. Processing
Automate your data preparation for faster, more precise analysis.Our platform takes the heavy lifting off your plate. It automates deduplication and normalization to keep your data clean and consistent, while custom rules help filter false positives and apply your own classifications. AI-driven entity extraction pulls key insights—like threat actors, malware, and attack patterns—from unstructured reports. For safer, faster analysis, our Malware Sandbox detonates suspicious files in a secure environment, extracts IOCs, and correlates them automatically. Built-in alerts surface critical intelligence, enabling quicker decisions and response.
-
4. Analysis
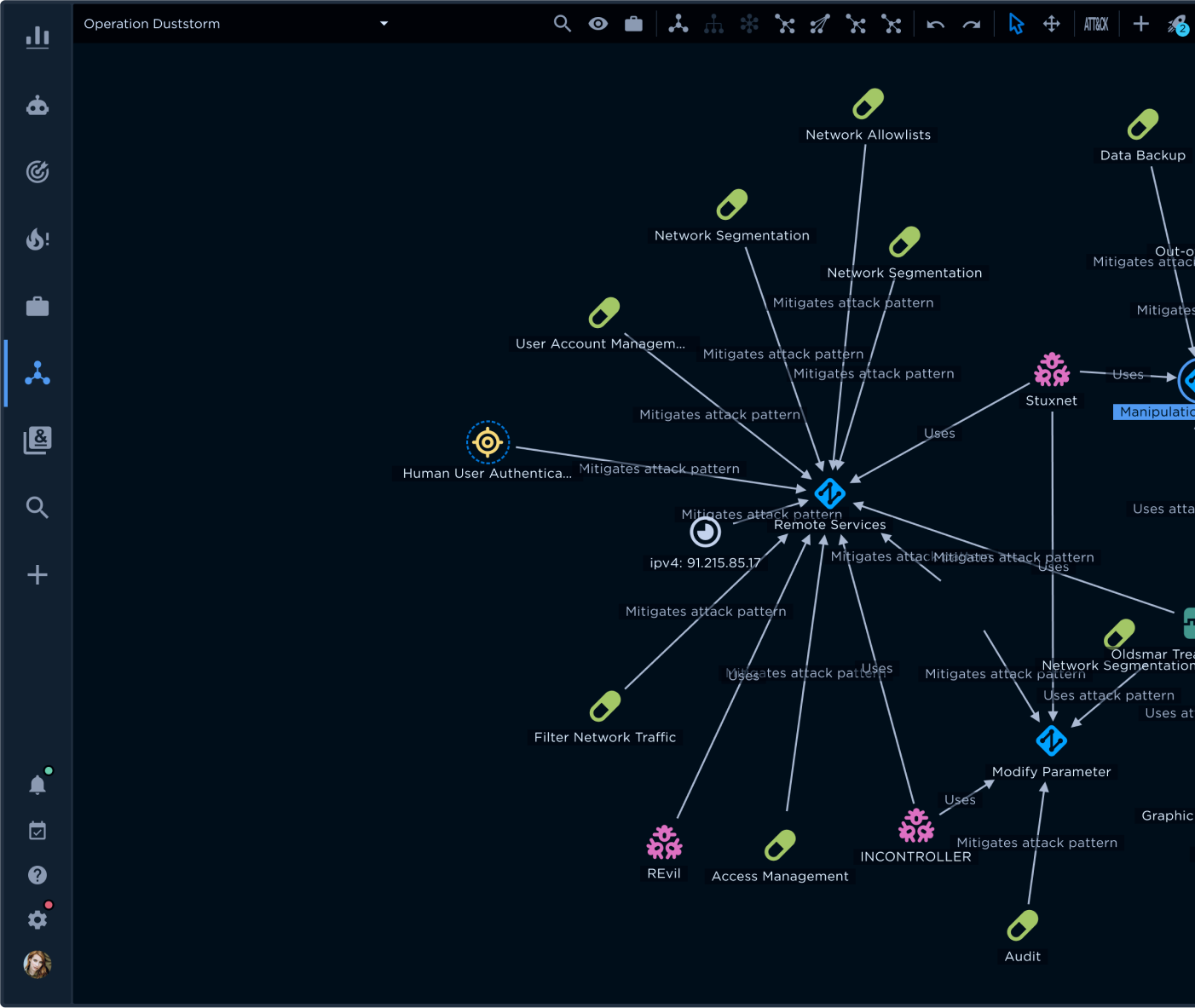
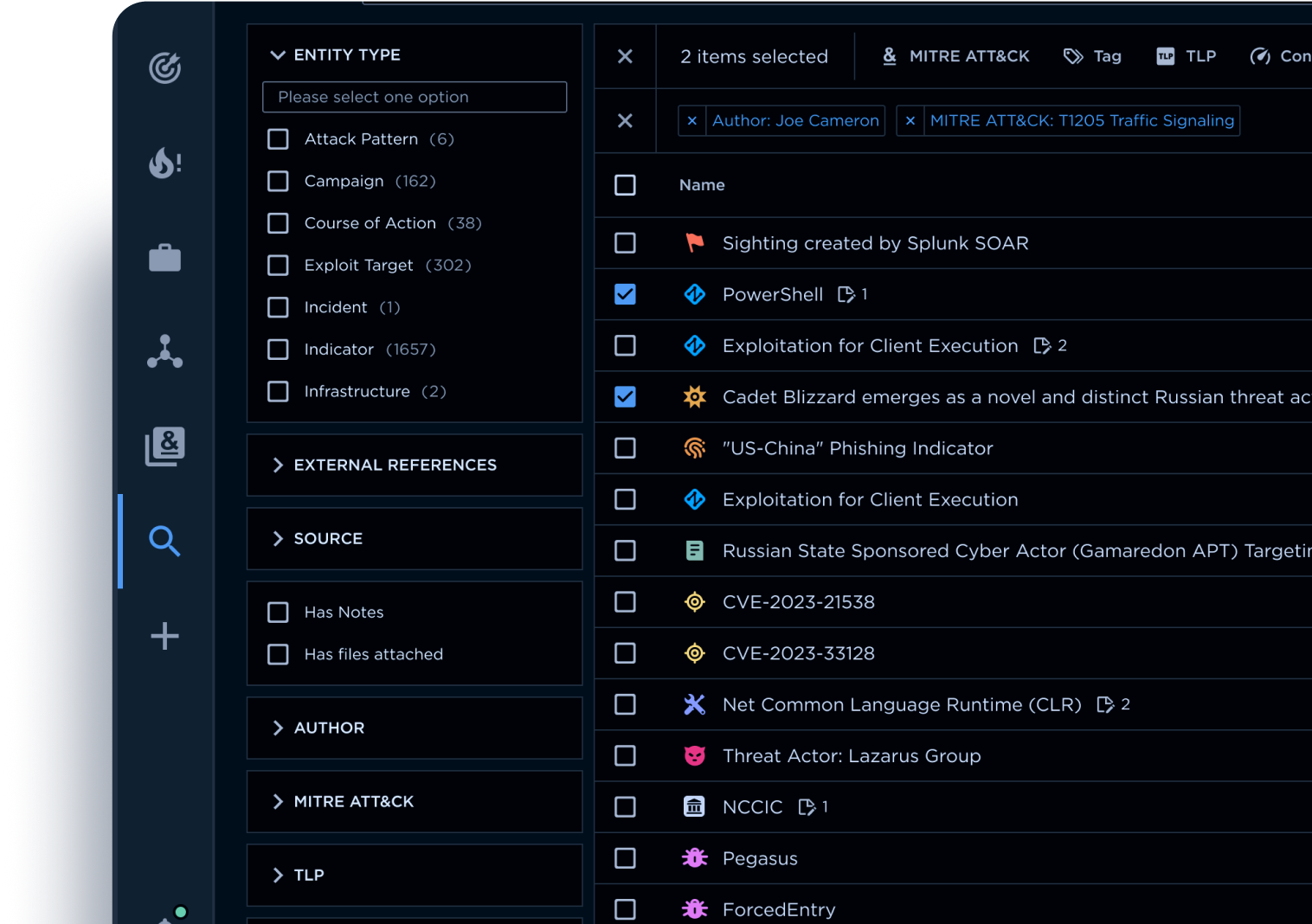
Turn raw data into actionable intelligence.Our advanced tools allow you to dive deep into your data and extract meaningful insights. Use powerful search and query features to explore your intelligence base, and visualize attack trends and TTPs with the MITRE ATT&CK Navigator, heatmaps, and dynamic graphs. Collaborate easily in dedicated workspaces, track ongoing threats with customizable watchlists, and monitor your security environment with intuitive dashboards. Accelerate investigations with the AI Assistant—instantly extract key details, summarize intelligence, and surface relevant external insights. Our TIP gives you everything you need to analyze and act on intelligence effortlessly.
-
5. Actioning & production
Create intelligence or directly transform insights into action.Learn more5. Actioning & production
Create intelligence or directly transform insights into action.Whether you need to take immediate action - like blocking malicious IPs on your firewall - or generate detailed intelligence reports, our platform has you covered. Use native reporting tools with rich text and media, or let AI automate report generation. Automate routine tasks, organize data with tags and rules, and collaborate seamlessly with built-in tools for tasks, notes, and annotations. This enhanced communication ensures your team stays aligned, while easy sharing features allow you to distribute validated intelligence swiftly across security tools and teams for immediate action.
-
6. Dissemination & feedback
Share intelligence with the people who need it, when they need it.Learn more6. Dissemination & feedback
Share intelligence with the people who need it, when they need it.Our platform offers flexible sharing options, whether it's internally with your team or externally with partners. With support for various formats - STIX, HTML, CSV - and a full REST API, you can tailor how and when intelligence is shared. Use our export filters to manage authentication, anonymization, and timing, ensuring secure and efficient distribution of critical information.
How you can use our TIP
How our TIP helps your team
-
CTI Analysts
Streamline your threat analysis with prioritized, contextual intelligence that reduces data overload and enhances detection.Explore our platformOur platform offers:-
-
-
-
-
SOC Analysts
Reduce alert fatigue and accelerate incident response with real-time, actionable intelligence tailored to your operational needs.Explore our platformOur platform offers:-
-
-
-
-
Cybersecurity Leaders and CISO
Safeguard your organization with intelligence-driven decision-making.Request a strategic consultationOur platform offers:-
-
-
-
-
MSSPs
Deliver scalable, differentiated threat intelligence services with automation and customized insights that enhance client value.Discuss potential partnershipOur platform offers:-
-
-
-
Learn more about Intelligence Center
Talk to one of our experts