Platform Overview
Discover our unique approach to Intelligence, Automation and Collaboration.
The most targeted organizations in the world use EclecticIQ Platform to automate threat intelligence at scale and accelerate collaboration across security teams.
-
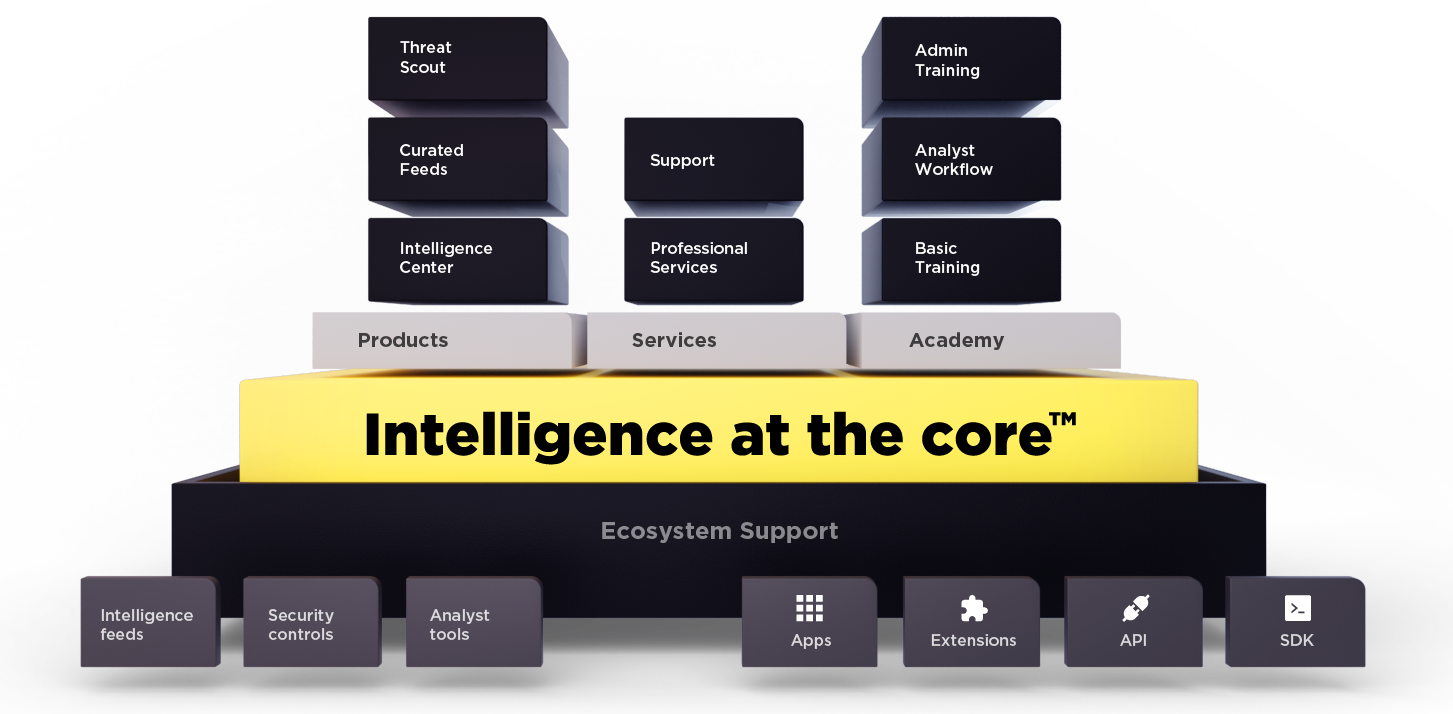
Intelligence at the core™
We put cyber threat intelligence at the heart of everything we do so you can stay ahead of the fast-changing ... Read more
We put cyber threat intelligence at the heart of everything we do so you can stay ahead of the fast-changing threat landscape. Our focus on intelligence and engaging with world-leading cyber security partners helps your organization gain greater insight, understanding, proactivity, efficiency, and confidence.
-
Products
EclecticIQ Platform helps you solve your threat intelligence ... Read more
EclecticIQ Platform helps you solve your threat intelligence challenges via modular products that offer best-of-breed capabilities and work together seamlessly.
-
Packages
Our modular products are available in a variety ... Read more
Our modular products are available in a variety of pre-configured packages suited for diverse use cases and can be customized to your specific needs.
-
Ecosystem
EclecticIQ Platform is extensible and customizable via robust developer tools and a long list of third-party integrations, giving you ... Read more
EclecticIQ Platform is extensible and customizable via robust developer tools and a long list of third-party integrations, giving you the flexibility to meet your specific requirements.
-
Services
As an EclecticIQ customer, you have access to a wide range of high-value ... Read more
As an EclecticIQ customer, you have access to a wide range of high-value services, such consulting, architecture guidance, and deployment support. These services complement and enhance our products, helping you get the most from your investment.
-
Academy
This in-house training facility is dedicated to helping you and your ... Read more
This in-house training facility is dedicated to helping you and your staff master our products. Courses incorporate guidance and content from our internal threat research team and external CTI experts.
-
EclecticIQ Platform and Packages
Discover our unique approach to Intelligence, Automation and Collaboration.
Download Product Description



