Log4j Zero-Day Vulnerability (CVE - 2021 - 44228)
Threat Intelligence Rapid Alerts
Rapid Alert #2
Nation-State and Ransomware Groups Leverage Log4j Exploit
Published date: 15/12/2021
CVE-2021-44228 is a remote code execution (RCE) vulnerability in the Apache Log4j library, a Java-based logging tool used by a significant number of applications globally (1). All versions from 2.0-beta9 through 2.12.1 and 2.13.0 through 2.14.1 are affected. A public proof of concept (POC) exploit was uploaded to Github on December 9th, 2021 (2) but in the wild exploit activity has been observed since at least December 1st, 2021 (3).
The vulnerability stems from Log4j’s use of Java Naming and Directory Interface (JDNI) lookups (4). JNDI is a Java API that allows the user to lookup data and resources using various protocols such as LDAP or DNS (4). The vulnerability exists as an attacker can insert a string into a JNDI lookup, in a user-agent for example, and retrieve a malicious Java class file executing the code remotely. The string must contain a colon (‘:’), this will cause the function to return the entire string in the JDNI lookup and load it into memory. The returned Java class file can then contain a reference to a second stage payload which will be downloaded and executed onto the system.

Figure:1.1: Format of malicious JNDI lookup
Nation-State and Criminal Groups are Leveraging CVE-2021-44228 to Deliver Malicious Payloads
EclecticIQ Threat Research Team has observed the cryptominer Kingsing, the IoT bot Muhstik, the Linux bot Mirai and the remote access trojan OrcusRAT in our dataset, being dropped and executed after exploitation of CVE-2021-44228. Kingsing and Mirai are currently the most prevalent payloads being dropped. Actors are using various obfuscation techniques to bypass current detection methods for the exploit. For example, the string below was observed in a user-agent; the string separates the ‘jndi:ldap’ section of the lookup to improve its chances of evading pattern-based detection.
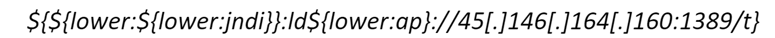
Figure 1.2: Example of obfuscated JNDI lookup
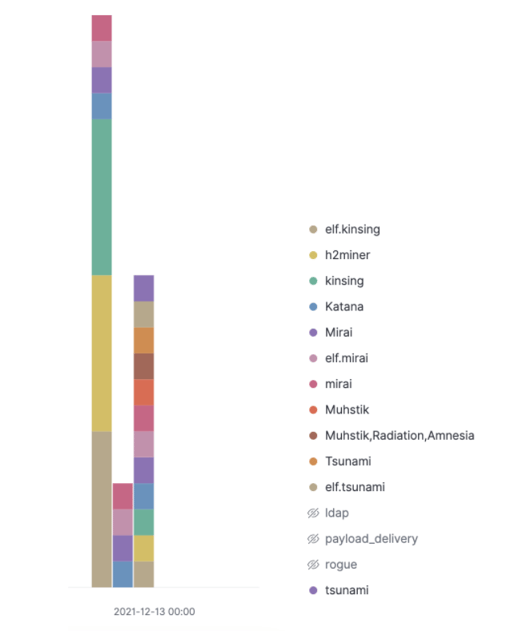 Figure 1.3: Bar chart of observed payloads related to exploitation of CVE-2021-44228 – 2021/12/13 onwards
Figure 1.3: Bar chart of observed payloads related to exploitation of CVE-2021-44228 – 2021/12/13 onwards
Exploitation of CVE-2021-44228 also enabled the deployment of Cobalt Strike beacons on exploited systems (5). Access brokers involved with ransomware-as-a-service have begun exploiting the vulnerability to gain initial access to networks (5). A new ransomware family named Khonsari has been detected trying to deploy after the exploitation of the log4j vulnerability on a system running Microsoft Windows (6). Exploitation has also led to the deployment of a reverse bash shell (6). An unidentified threat actor has been observed inputting JNDI lookups in the header, subject line, and body of an email attempting to exploit CVE-2021-44228 (7). It is unknown whether this was successful.
Nation-state groups originating from China, North Korea, Turkey and Iran have been observed exploiting CVE-2021-44228 (5). Chinese government actors used the log4j vulnerability to breach targets (8), with Microsoft reporting that HAFNIUM, a nation state group operating out of China, has leveraged the vulnerability to use a DNS service typically used to fingerprint systems (5). PHOSPHORUS, an Iranian actor tracked by Microsoft previously been seen deploying ransomware, has acquired and made modifications to the log4j exploit (5).
Widespread Use of Log4j Provides Large Attack Surface for State-Backed and Criminal Actors
It is certain that widespread exploitation of CVE-2021-44228 will continue. The ease of exploitation alongside the widespread use of log4j in many enterprise technology stacks provides a low barrier to entry and wide threat surface for attackers to perform RCE. Cryptominers and botnets will almost certainly remain widespread. More advanced payloads such as Cobalt Strike will almost certainly increase in popularity, which will increase the ransomware threat.
EclecticIQ recommends that users inventory their systems and identify software that use vulnerable versions of log4j in their environment, and patch immediately to the latest version 2.16.0 as 2.15.0 is vulnerable to CVE-2021-45046 (9). Users should prioritize patching vulnerable public facing systems over vulnerable internal systems. If unable to patch, isolate vulnerable systems if they are publicly available and apply the official mitigations (10). Users should not use the Java version as a form of mitigation as that has now been bypassed (11). It is recommended that system defenders focus hunting efforts related to CVE-2021-44228 back to at least December 1st, 2021. For a list of currently known affected software, detection content and scanning tools visit the Github repository maintained by NCSC-NL (12).
References:
- https://nvd.nist.gov/vuln/detail/CVE-2021-44228
- https://github.com/tangxiaofeng7/CVE-2021-44228-Apache-Log4j-Rce
- https://twitter.com/eastdakota/status/1469800951351427073
- https://logging.apache.org/log4j/2.x/manual/lookups.html#JndiLookup
- https://www.microsoft.com/security/blog/2021/12/11/guidance-for-preventing-detecting-and-hunting-for-cve-2021-44228-log4j-2-exploitation/
- https://businessinsights.bitdefender.com/technical-advisory-zero-day-critical-vulnerability-in-log4j2-exploited-in-the-wild
- https://blog.talosintelligence.com/2021/12/apache-log4j-rce-vulnerability.html
- https://www.reuters.com/technology/widely-used-software-with-key-vulnerability-sends-cyber-defenders-scrambling-2021-12-13/
- https://nvd.nist.gov/vuln/detail/CVE-2021-45046
- https://logging.apache.org/log4j/2.x/security.html
- https://twitter.com/Laughing_Mantis/status/1470412026119798786
- https://github.com/NCSC-NL/log4shell
Rapid Alert #1
Log4j Zero-day Actively Exploited in the Wild
Published date: 10/12/2021
Yet-unidentified threat actors are actively exploiting CVE-2021-44228 in the wild (1), a zero-day in the Java logging library Apache Log4j (2). The vulnerability is classed as ‘severe’ and allows an actor to perform unauthorized remote code execution (RCE). Systems running versions between 2.0 and 2.14.1 of the Java logging library Apache Log4j are affected.
The vulnerability is severe due to the widespread use of the Log4j application for logging (3), the ease of using the exploit, the impact of the exploit, and the fact that actors are actively leveraging the vulnerability.
Any organization running Apache Log4j should assume a breach mentality and review logs for remediation. Organizations should upgrade all affected systems to Log4j version ‘log4j-2.15.0-rc1’ as soon as possible. If unable to upgrade, users should follow the steps in the official Apache mitigation guide (4).
References:


